

Securing automation and related OT systems and their components has been a major area of focus for many years. Much of this attention has focused on improving security and reducing the risk to installed systems. While this is certainly important, it is no longer sufficient. OT systems are often complex, including components from a wide range of hardware and software suppliers. Those who operate, support, and service these systems also use a variety of tools for their purposes. The supply chains used to procure and support these systems may have vulnerabilities that lead to significant security risks.
Identifying and addressing these risks was the subject of a workshop conducted as part of the 26th annual ARC Forum in Orlando. Speakers Michael Fabian of Synopsys Software Integrity Group and Klint Walker of the Cybersecurity and Infrastructure Security Agency offered specific guidance on how to address these risks, and panelists Sandra Parker of Dow, Glenn Aydell of BASF, and Torey Smith of Hemlock Semiconductor shared their perspectives.
There are several potential risks to OT systems that are associated in some way to the supply chain. A supply chain incident happens when the components that make up the OT system are compromised. This was demonstrated in the recent Solarwinds attack. In this case, a software company that sells network management tools had their servers compromised, causing them to update customer’s computer systems with software that had malicious software, which in turn infiltrated their customer’s systems.
Although this is one of the more recent and well covered supply chain incidents, it is neither unusual nor unprecedented. Attacks of this type are becoming more common, with more widespread consequences. They often exploit zero-day vulnerabilities such as Log4J, which was identified in 2021.
Although many supply chain incidents involve software vulnerabilities, a hardware supply chain risk can also be present if hardware components of an OT system are compromised. Components may have embedded malicious software or may be counterfeit, having functionality and appearance similar to the original, but with backdoor access that may be invoked any time. When acquiring hardware from third parties or distributors it is very important to verify their provenance.
Irrespective of whether the vulnerabilities involve hardware or software, the level of risk is elevated simply by the nature of the targeted systems or applications. Risk is generally defined in terms of threat, vulnerability, and consequence. For OT systems the possible consequences can be much more serious. They typically have access to in-depth knowledge of the system or process under control. This knowledge would have been difficult to obtain from an outside perspective.
In considering security risks to OT systems, it is common to think first about industrial control systems, consisting of controllers, sensors, logic solvers and associated communications processors. Systems for manufacturing operations such as historians, engineering workstations and multi-variable controllers also require attention, particularly since they typically exchange information with business IT systems. These include those used for inventory and supply chain management and optimization. Since these systems are connected to the enterprise network, they may represent an additional attack vector.
It is not sufficient to simply acknowledge the existence of supply chain related risks. Additional analysis is required to fully appreciate the nature of those risks and prepare an effective response.
Michael Fabian of Synopsys Software Integrity Group discussed this in the Forum workshop in Orlando. One of his key messages was that the perspective must broaden from simply focusing on the processes used to develop products and systems to include all aspects of the supply chain. This message is summarized in figure 1.
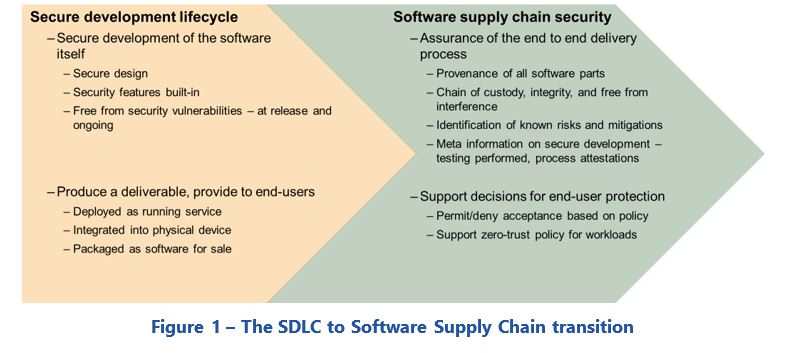
Michael suggested that this broadening of scope leads to the need to answer several fundamental questions, including:
Taking the time to prepare thoughtful answers to these and similar questions helps to better plan an effective response.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Availability, Cybersecurity, IT, Manufacturing Operations, OT, Risk, Supply Chain, ARC Advisory Group.

