

Keywords: OT Cybersecurity, Asset Information, Cyber Compliance, Industrial Defender, ARC Advisory Group.
Cybersecurity has never been more important or more challenging for manufacturers and critical infrastructure operators.
Industrial companies need to be sure that their industrial control system (ICS) security programs can deal with these challenges. A  single cyber incident could jeopardize safety, business continuity, and the organization’s survival. Inadequate attention to compliance requirements can lead to significant financial penalties and the loss of a facility’s license to operate.
single cyber incident could jeopardize safety, business continuity, and the organization’s survival. Inadequate attention to compliance requirements can lead to significant financial penalties and the loss of a facility’s license to operate.
Complete, accurate asset information is essential for understanding control system cyber risks and the effectiveness of existing security practices. To be effective, asset information must include a complete listing of every system element, including endpoints and network components, as well as detailed information about each device’s hardware, firmware, and software configurations. Development and management of this information is time-consuming and requires a solution that automates data collection, detection of changes, and preparation of information for management and compliance.
This paper describes the capabilities that end users should consider in developing an asset information strategy. A review of Industrial Defender’s solution is included to show how one industrial cybersecurity company helps companies meet these requirements.
ARC’s Industrial/OT Cybersecurity Maturity Model provides a useful tool for understanding and managing the status of industrial cybersecurity programs. This model provides a roadmap for implementing the security technologies and human resources needed to support the NIST cybersecurity framework recommendations.
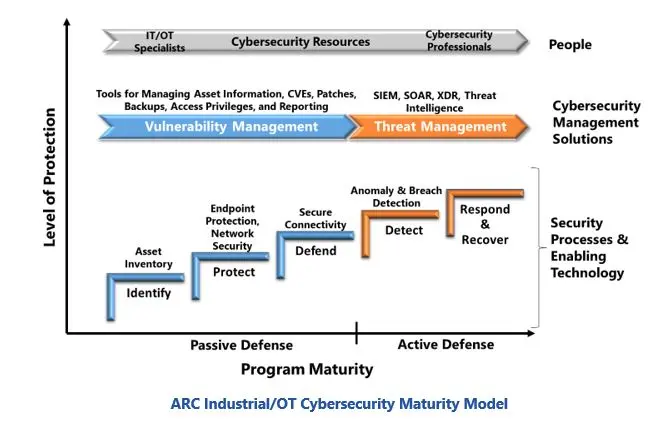
The steps in ARC’s model reflect the sequence that companies should follow in security technology investments. This ensures that solid, foundational capabilities are in place to support the requirements of subsequent steps. The colors in the model distinguish passive defensive measures that are needed to protect systems against conventional hackers, from the active defense capabilities needed for more sophisticated attacks.
A key benefit of the ARC model is how it highlights the need to maintain alignment of people, processes, and technology capabilities. The effectiveness, or maturity, of a cybersecurity program is determined by the category with the lowest maturity score.
ARC’s model also emphasizes the need for investments in asset information and cybersecurity management solutions to ensure that limited security resources can efficiently assess security posture, maintain defenses, manage attacks, and prepare management and compliance reports. Many companies have underestimated the importance of these capabilities and are operating critical facilities that remain at risk of serious cyber incidents.
ARC’s model shows how effective security programs are built through specific, incremental investments in people, process, and technology capabilities to achieve certain security goals. Decisions in each step rely on information collected in the initial Identify stage. This includes the information collected about devices, configurations, vulnerabilities, threats, and compliance requirements. Completeness and accuracy of this asset information has a direct impact on overall program effectiveness. For example, incomplete information limits the ability of detection solutions to provide actionable security alerts. So, defenders waste valuable time getting information that should have been readily available.
Cybersecurity maintenance needs information to maintain defenses as new security risks emerge in the environment. Environmental risks are generally monitored through feeds from sources that report common vulnerabilities and exposures (CVEs), patch releases, and threat actor activity. But accurate, detailed asset information is also needed to evaluate relevance and develop appropriate responses.
Defenders need accurate, detailed asset information to detect new risks that may emerge within systems through the actions of operators, maintenance personnel, or sophisticated attackers who evade facility defenses. Detecting changes in asset information is the only way of detecting many of these threats. Asset information completeness determines the kinds of threats that are detectable while frequency of data collection will determine how long these threats to facilities exist.
Compliance reporting and governance are burdensome security areas that can distract security teams from their primary cybersecurity management responsibilities. Having convenient access to complete, accurate asset information that supports regulatory and governance requirements is essential to avoid degradation of security defenses.
Given the critical importance of accurate, complete asset information ARC recommends that every industrial company ensure their asset information strategy supports the following requirements:
System Device Information – Complete, detailed information about every device involved in control system operation, including process controllers (PLCs, DCS, IEDs, etc.), user devices (HMIs, workstations, etc.), servers, and all active network devices. This should cover all the information that is relevant to understanding security status, selecting security defenses, and restoring devices in the event of a failure or compromise. This includes device identifiers; hardware, software, and firmware applications, versioning, and configuration settings; patch status; etc.
System Communications Information – Complete, detailed information about connections and data flows that exist between system devices and external resources. This information should be adequate to enable selection and configuration of network security solutions during security program development, and the detection of unauthorized changes and anomalous communications during the security maintenance phase.
System Changes and Events Information – Historical records of all changes and notable events that have occurred within the protected system. This includes information captured within system devices (syslogs, netflows, NAC credentials, etc.) as well as alerts generated by system security solutions. It should also include records of all changes detected by the asset information management system itself, like changes in PLC and DCS programs, firewall rules, etc.
Information Collection – Information collection should be automated to the maximum extent possible, with methods that allow frequent, non-disruptive detection of system changes. Passive network scanning methods are useful, but they don’t capture all the required information and don’t see isolated devices. Complete, accurate asset information requires a blend of data collection approaches that include intelligent active scanning to capture and monitor device configurations, agents within devices to capture anomalous activities, and bi-directional integration with other systems that can provide relevant asset information. Support for manual data collection is also necessary to collect information not amenable to auto data collection. This includes manual entry screens and ingestion of various kinds of data files (Excel spreadsheets, etc.).
Information Storage – Asset information is a critical resource and needs to be stored in ways that ensure proper protection yet broad availability to authorized users. Storage strategies should support multiple copies, periodic time-stamped archival, and rapid restoration of systems from trustworthy backup information.
Information Access – Convenient access to asset information is essential and needs to be supported for a variety of user perspectives and needs. Device lists by type and location are needed to plan patch deployments. But defenders also need rapid access to information through system maps and connectivity diagrams when they are responding to security alerts.
Security Management Support – Security management involves a variety of routine maintenance activities like evaluating Common Vulnerabilities and Exposures (CVEs), preparation of periodic compliance and management reports, and managing user privileges. Support for these kinds of activities should be included in the asset information system to minimize the workload of limited OT cybersecurity teams. There is a general shortage of these professionals and reducing time spent on non-critical tasks is key to ensuring that facilities address all the critical issues required to remain secure.
Industrial Defender is generally considered the first company to offer a cybersecurity management solution exclusively focused on industrial OT systems. In business since 2006, the company has developed a strong reputation for cybersecurity management in the power and process industries and has an extensive list of successful installations.
Industrial Defender OT Security Management Platform is purpose-built for industrial control systems and addresses the overlapping requirements of cybersecurity, compliance, and change management. This product provides the data collection and information management support that companies need through all phases of building and maintaining effective OT cybersecurity programs.
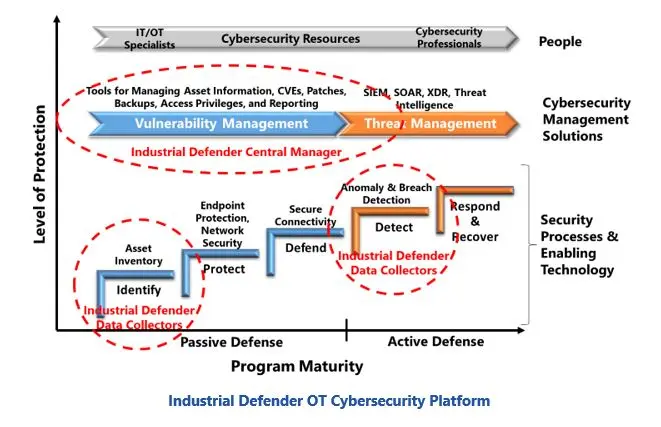
The deep functionality in Industrial Defender’s platform is enabled by their extensive focus on ensuring companies have the complete, detailed asset information needed to effectively manage OT system security. This includes detailed information about every control system asset, communication path, and event that occurs within the system. Unlike IT security tools, their product recognizes the differences in information requirements for traditional industrial controllers, like PLCs and DCS systems; industry specific control system elements like substation switches; networking devices like firewalls and switches; and conventional PCs and servers.
Following are some examples of detailed information that distinguish the breadth and the depth of Industrial Defender’s asset information content from IT-centric and passive asset discovery solutions:
Device Information - Serial number; OS, including version and patches installed; Firmware and software, including versions and vulnerabilities; Open ports and services; Removable media installed; CPU & RAM usage over time; Disk space; Swap space; etc.
Communication Information - Firewall rules, including change detection; Blocked execution (packet); Blocked unauthorized file; Generic and shared user accounts; Local and A/D accounts; Password parameters and age; etc.
Changes and Events – Configuration changes, historical context, deviations from known good baselines; and Log events including: Connectivity lost; Device Shutdown; Device Rebooted and boot checksum; Backup failure; Failure of event logging; Successful and failed login attempts; User account locked; Privilege raised; Failure of event logging; Policies modified; etc.
The Industrial Defender platform includes a variety of automatic and manual data collectors that enable users to acquire this information, regardless of their specific situation. This includes manual entry by users and ingestion of files; passive monitoring (Industrial Defender or third-party network monitoring solution like Nozomi); native and agentless polling; and Database queries.
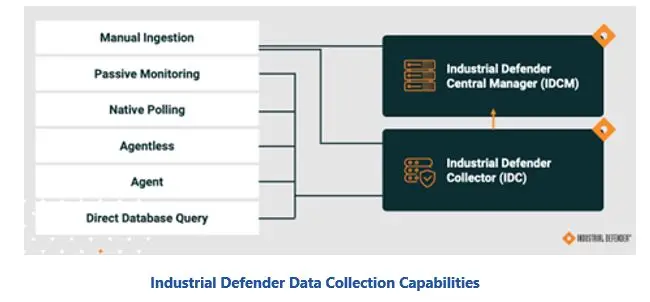
The Industrial Defender central manager aggregates all devices, communications, and event data from industrial endpoints across a variety of automation system products to provide a single, unified view of operations. The solution is also designed for periodic collection and comparison of information with previous baselines to detect control system changes for review and action by security teams. Historical records of all changes are also kept as an aid for security teams in their forensic efforts.
The central manager provides users with a variety of screens for accessing collected and historical information. This includes a top-level screen that highlights potential risks, and a full complement of screens for drilling down into all collected and derived detailed information. There is also a powerful search capability that enables ad hoc searches for assets that meet specific criteria, like manufacturer, etc.
Industrial Defender’s OT heritage is clearly demonstrated in the support capabilities they provide for security management. This includes a broad set of reporting templates for major industrial standards like NERC CIP, NIST CSF, IEC 62443, NIS, etc. Users can edit these templates to address their own needs and can create additional data templates for other information that they need for internal reporting. The company also offers a vulnerability management service that helps end users identify devices in their system that are at risk for known CVEs.
Accurate, complete asset data is essential for ensuring that industrial companies can defend systems against today’s challenging threat environment. Quick, convenient access to this information helps plants build and maintain effective cybersecurity programs.
Our review of Industrial Defender’s Cybersecurity Management Platform shows that there are companies who can help you establish the asset information capabilities needed for effective OT cybersecurity programs. The biggest risk to your OT security is ignoring the urgency in addressing this critical issue.
ARC Advisory Group clients can view the complete report at the ARC Client Portal.
Please Contact Us if you would like to speak with the author.
You can learn more about cybersecurity at Industrial Cybersecurity Market Analysis Research

