

The introduction of process safety system-specific malware into the manufacturing world in 2017 intensified the discussion around the convergence of safety and cybersecurity. If a cyber-attack could compromise safety in the physical world, we must view cybersecurity in the context of safety. Similarly, approaches taken in the safety world to evaluate risk and design safer systems must consider cybersecurity-related threats to the integrity of safety systems.
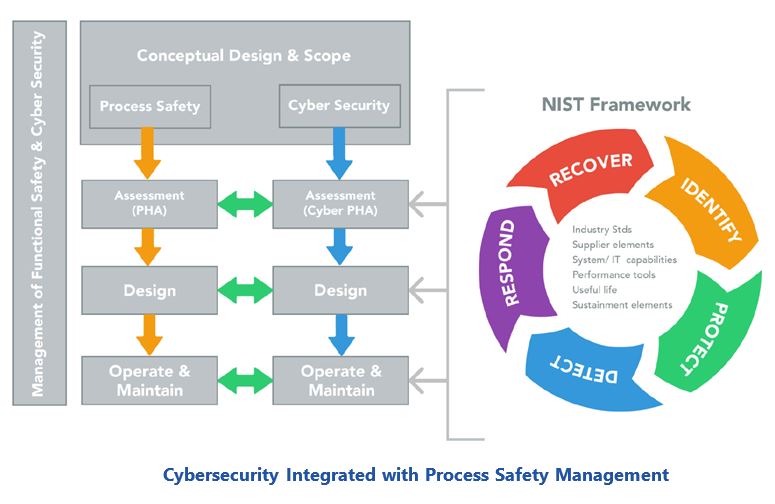
Key end user clients from the oil & gas, marine transportation, and offshore exploration and production industries discussed these and related issues in a session at the 2019 ARC Industry Forum in Orlando. In this session, Mark Duck, with the Shell Projects & Technology organization, talked about an approach they are exploring to integrate cybersecurity risk assessment into traditional process hazard analysis (PHA) methods. For example, hazard and operability (HAZOP) studies could be used to determine the impact of cyber-security threats and vulnerabilities on the safety of plant operations. Similarly, methods like HAZOP should be adapted to consider the cybersecurity risk to the integrity of the selected safety barriers for each specific hazard risk scenario.
These approaches are not limited to the oil & gas industry and could be applied to an even wider range of industries, including those that are not the primary users of process safety systems.
The industry needs: 1) a clear way to think about how cybersecurity risk, if realized, could degrade the integrity of safety barriers, and 2) a standard methodology to assess this risk. In the first case, using a bow-tie model and the concept of escalation factors can help frame where cybersecurity threats and vulnerabilities can affect safety barriers. In the second case, the industry has already taken steps to address how cybersecurity risk assessment can be integrated into the functional safety lifecycle.
For example, the IEC 61511 Functional Safety standard now requires a SIS security risk assessment. ISA has also published a technical report (ISA-TR84.00.009-2017) that documents a SIS cybersecurity risk assessment procedure, called cybersecurity PHA or cyber PHA. The link to PHA is a step in the cybersecurity risk assessment process to: 1) review the output of the PHA to identify worst-case HSSE consequences for the asset, and 2) identify any hazard scenarios where the initiating event and all control barriers are “hackable.”
NAMUR has also published a worksheet (NA 163) titled “Security Risk Assessment of SIS.” A Cyber PHA methodology can be used to assess the risk associated with identified cybersecurity-related escalation fac-tors and recommend mitigations to reduce the risk to an acceptable level. Linking concepts and tools used in the process hazard analysis world with cybersecurity risk assessment can help bring these two, traditionally separate, risk management processes together with a goal of improving the robustness of our safety systems against cybersecurity attacks.
Most cybersecurity risk scenarios only result in a consequential business loss consequence along with potential impact on reputation. PHAs typically do not consider consequential business loss, but a cybersecurity risk assessment must include this consequence category as shown in the example risk assessment matrix. This consequence category can be calibrated in terms of duration of production loss. The worst-case severity is calibrated by determining the maximum number of hours, days, weeks, etc., it would take to bring production back online in case of, for example, a ransomware attack that impacts all servers and work-stations in the industrial automation and control system (IACS). The cost would be the value of lost/deferred production plus the materials and labor required to respond to the incident. The list of systems required to bring production back online will likely be a subset of all systems in IACS. From a cybersecurity risk scenario point of view, this list would be the critical systems, including all safety systems.
Shell is well known for its emphasis on safety. The company takes a comprehensive and multifaceted approach to managing process safety risk including managing the HSSE risk associated with the asset process (a particular aspect of the chemical manufacturing process for example), integrity of safety barriers, risk to production loss, and other factors.
Shell uses many methods to evaluate risk in process safety that are consistent with those outlined in the ISA 84/IEC 61511 process safety standard. These include the use of risk assessment matrices that consider likelihood; consequence of risks to people, assets, community, and environment; and severity of the consequence. The company also uses bow-tie models to visualize the various elements of risk scenarios such as hazards, top events, barriers, etc., including escalation factors and escalation factor controls.
A “Hazard” is an agent with potential to cause harm. A “Top Event” is an uncontrolled release of a hazard such as hydrocarbons, toxic sub-stances, energy, objects at height, etc. An “Escalation Factor” is any situation, condition or circumstance that may lead to the partial or full failure of a barrier (e.g., independent protection layer). An example of this would be making unauthorized trip setting changes to a safety instrumented function. This escalation factor could be controlled by improving the logical and/or physical access controls for the safety instrumented system. Identification of escalation factors is part of the process of managing the integrity of independent protection layers. These tools, among others, can be used to start the journey of integrating the process safety and cybersecurity risk assessment processes.
Today’s challenge is to create an interface between process safety risk assessment methods and cybersecurity risk assessment methods. Historically, the HSSE risk assessment process has not considered sabotage (cybersecurity attacks are a form of sabotage). Given the level of sophistication seen in recent cybersecurity attacks on industrial control systems, the potential for simultaneous cybersecurity attacks on one or more independent layers of protection must be considered during the HSSE risk assessment process.
Safety instrumented systems and other control and recovery barriers have cybersecurity vulnerabilities that must be mitigated. These vulnerabilities represent “Escalation Factors” in the Bow-tie Model that must be mitigated with appropriate “Escalation Factor Controls. “(See bow-tie model above.)
One possible interface between the Cybersecurity Risk Assessment and the HSSE risk assessment process is to focus on cybersecurity Escalation Factors associated with barriers that have cybersecurity vulnerabilities. One advantage to this approach is that it is already part of the existing HSSE risk assessment process.
It is common for one or more of the selected control or recovery barriers to be vulnerable to cybersecurity threats. Some examples are safety instrumented systems, PLC-controlled fire water pumps, fire and gas systems, etc.; essentially any barrier based upon microprocessors running firmware/software and, potentially, connected to a network. A cyber-security escalation factor for these types of controls is the combination of cybersecurity threats and vulnerabilities associated with the equipment used to implement the control. In this context, cybersecurity escalation factors are just one type of escalation factor among many other types of escalation factors that can degrade the integrity of a safety barrier.
During a PHA, there is the possibility that the initiating event and all the control barriers selected for a hazard scenario have cybersecurity escalation factors. Where this is a high-consequence scenario (e.g., potential fatality), an effort should be made to add at least one control barrier that does not have cybersecurity escalation factors such as a pressure relief valve or non-programmable safety instrumented function (SIF). If this is not possible, the cybersecurity risk assessment team should consider that a cybersecurity attack on these specific control barriers has a higher likelihood of leading to the top event and identify a robust set of cybersecurity countermeasures to manage this risk.
Industrial assets typically have a maintenance program to maintain the various components of the asset and must often prioritize work based upon some criteria. A common way to do this is to organize the assets in terms of system criticality. If a backlog of maintenance activities exists, then one would ensure the components with the highest criticality are taken care of first.
A common issue with cybersecurity controls in an ICS environment is the related maintenance required to sustain them over time. Often, the maintenance associated with cybersecurity controls is a lower priority than instruments, valves, etc. because of the lower perceived value. One way to resolve this issue is to assign the cybersecurity controls, used to manage cybersecurity escalation factors, a criticality rating based on the barrier being protected and then factor this into the overall maintenance strategy.
The need for doing cybersecurity risk assessments for process safety is called out in IEC 61511 Part 1 (2016). This requires that “a security risk assessment shall be carried out to identify the security vulnerabilities of the SIS.” The requirement further specifies additional details supporting the risk assessment. While this is a needed step, there are potentially many other safety systems, in addition to SIS, that are subject to cybersecurity vulnerabilities.
The following are examples of other programmable safety systems that are subject to cybersecurity vulnerabilities:
The trend to integrate these programmable safety systems with basic process control systems will likely continue and must be considered in the context of the IEC 61511 safety lifecycle, which includes ensuring cybersecurity risks are adequately addressed. Considering these challenges, companies must ensure that cybersecurity risks to the availability of all barriers are understood, mitigated and even “designed out,” where possible, during the PHA process.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Cybersecurity Safety, Process Safety, HAZOP, Marine, PHA, LOPA, Shell, ARC Advisory Group.

