

Increasingly, end users in the industrial and critical infrastructure sectors seek products and solutions that are inherently cyber-secure. In many cases, cybersecurity provides the catalyst for control system modernization projects. This is particularly true in cases where users discover they no longer can support an installed base that requires an increasing amount of time and resources to make it cyber-secure.
To date, much of the focus on cybersecurity for industry and infrastructure has focused on providing layers of cybersecurity on top of existing infrastructure, rather than procuring products and applications that provide a level of inherent cybersecurity. Inherent cybersecurity is often achieved through some combination of product design features and a secure development lifecycle process. From the supply chain perspective, many end users are also looking to source inherently secure components, microprocessors, and embedded systems.
In addition to closer scrutiny of suppliers during the selection process, the built-in, secure-by-design approach also requires secure implementation, installation, and maintenance approaches throughout the lifecycle of the system or product. Two separate but related lifecycles are at play here: one for product development and one for implementation and support. Looking for products that are certified to a cybersecurity standard, like the ISA/IEC 62443 series of standards, can also be a challenge since many users are unfamiliar with the various certification and standards bodies. While even products that are not certified to a published standard can sometimes provide acceptable cybersecurity, this requires closer scrutiny of vendor offerings and their associated development and sourcing practices. Using certifications to help pre-qualify potential products can save asset owners considerable time and effort.
Most OT-level products and applications in industry and critical infrastructure worlds are not designed from the ground up to incorporate cybersecurity. Until relatively recently, features, functions, and open network connectivity have received much more attention. The drive toward “openness” in the 1990s and early 2000s resulted in a cybersecurity mindset focused on adding layers of cybersecurity in operational technology (OT)-level systems to address vulnerabilities. While this mindset is still required for effective cybersecurity, many end users are finding that it is much easier and less costly to invest in products that are designed from the ground up to incorporate security rather than increase investments to lock down products that are not secure.
Security by design should go beyond the products themselves and how they are designed to incorporate secure development lifecycle practices for applications. The same principles apply to the processes used in control system engineering, installation, and startup. End users are also taking a closer look at the security of the supply chain, specifically in how systems are developed and manufactured, and if the systems utilize secure components and embedded systems.
The new wave of Industrial IoT-enabled products such as edge computing devices; cloud computing platforms; and smart, connected sensors provides an additional level of complexity for end users from a cybersecurity perspective. While many of these “industrial edge” offerings incorporate good cybersecurity, such as “zero trust” architectures, others do not. Since many of these offerings are making their way from the IT world into the OT world, they must be even more closely scrutinized to evaluate cybersecurity risk.
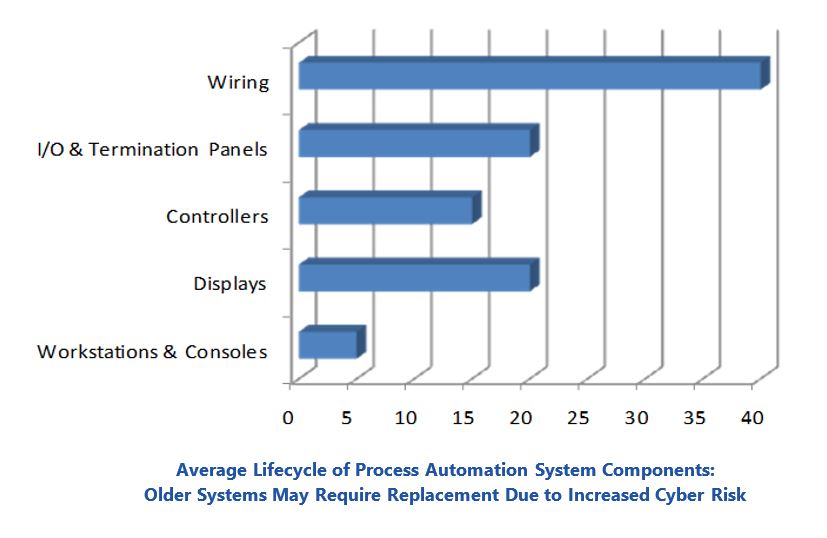
Control systems in industrial and critical infrastructure environments typically have extremely long lifecycles. Many DCSs and PLCs have been in service for 20 years or more. Many end users are finding that the older installed base is too complex, costly, and risk-prone to continue to support from a cybersecurity perspective. This often provides the primary impetus for a control system migration or modernization project.
The ISA/IEC 62443 series of standards are the key cybersecurity standards for manufacturing and critical infrastructure. The series is recognized internationally and the product of decades of work by end users and suppliers alike. While the initial focus of the standards was on describing reference architectures and fundamental concepts like defense-in-depth, the 62443 standards today encompass all aspects of industrial cybersecurity, from product and application development through the complete lifecycle.
The 62443-4-1 standard specifies process requirements for the secure development of products used in industrial control systems (ICS). It defines a secure development lifecycle (SDL) for developing and maintaining secure products. This lifecycle includes the following practices:
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Secure-by-Design, OT Cybersecurity, Modernization, Defense-in-Depth, ARC Advisory Group.

