

Cybersecurity supplier Claroty recently released version 3.5 of its Continuous Threat Detection (CTD) security monitoring and risk assessment offering for both IoT and OT devices. Claroty is acknowledging that the lines between industrial Internet of Things (IoT) and operational technology (OT) are increasingly blurring. Many end-users in the manufacturing and infrastructure segments are adopting IoT technologies, these technologies are increasingly touching critical processes, and cybersecurity must be a priority to keep connected assets and processes safe. In addition to bridging the gap between IoT and OT domains, Claroty also touts faster deployment features and a new machine learning (ML) alert algorithm that promises to cut down on unnecessary alerts.
According to ARC’s own research, millions of IoT devices are finding their way into OT networks and environments. End users are increasingly concerned with balancing the risk of adopting these new technologies with the technology advantages and the business value proposition they provide. With the new version of CTD, Claroty is aiming to manage these risks by offering a cybersecurity solution for both managed and unmanaged IoT assets.
CTD now automatically discovers and classifies any and all IoT devices on a network, correlates these devices with known vulnerabilities, and continuously monitors them with Claroty’s five detection engines. Claroty’s interface semi-automatically augments protocol support for new devices in the field. The result is full-spectrum, unified visibility across IoT and OT devices at no risk to operations.
Segmenting your networks can provide a lot of benefits, but the actual implementation can be difficult and time-consuming. CTD’s new Virtual Zones+ feature automatically tags assets with similar network traffic parameters into logical groups. Once grouped, CTD identifies the relationships between logical groups and automatically generates granular communication policies. The policies assign permission levels to each zone, along with a specific level of trust to help the end-user understand the risk posed by every logical connection between the zones. Anomaly-based alerts indicate a breach of this trust.
Establishing baseline communications between assets in automatically designated virtual zones can rapidly accelerate and bring down the cost of network segmentation projects. CTD’s firewall integrations with Palo Alto, Cisco, CheckPoint, and now Fortinet allow customers to enforce network segmentation policy violations proactively by identifying and restricting anomalous or non-compliant communications across zones.
Many security tools deliver alerts to the SOC without any context surrounding their origin. CTD’s new Root Cause Analytics feature provides customers with visibility into the chain of events leading up to every single alert. This is particularly important for OT security alerts consumed by IT security professionals with limited to no knowledge of OT operations. This enables faster and easier triage of alerts and makes proactive threat hunting easier with the context surrounding the associated threat and risk provided.
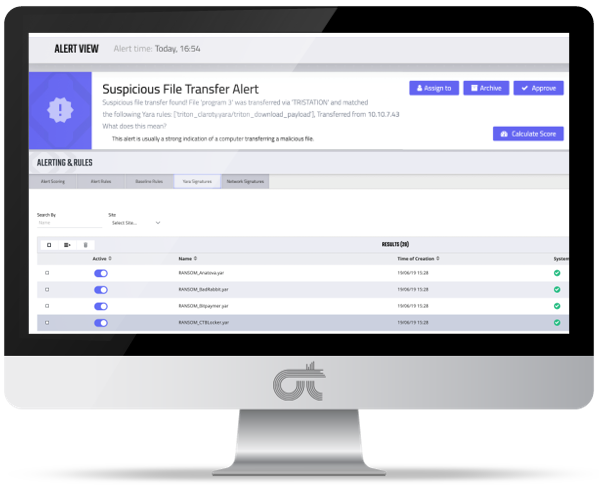
When it comes to OT and IoT security, relevant and actionable threat intelligence is increasingly valuable. CTD V3.5 includes Claroty Threat Intelligence (CTI), a highly curated, multi-source, and tailored feed that builds on Claroty’s Root Cause Analytics with proprietary research and analysis of OT zero-day vulnerabilities and ICS-specific indicators of compromise (IoC) linked to adversary tactics, techniques, and procedures (TTP). CTI’s YARA rules, for example, run on OT asset configuration changes and code sections, not just IT artifacts. Powered by Team82, Claroty’s research and development (R&D) arm, CTI equips threat hunters and incident responders with the relevant context needed to detect and prevent targeted attacks early in the kill chain and mitigate the consequences of malware infections.
ClarotyOS is a purpose-built, hardened Linux OS that requires no more than a few basic configurations before CTD can start discovering assets, extracting granular attributes, and learning their communications. The new ClarotyOS and System Dashboard features enable faster deployment of CTD on rack mount and DIN-rail form factors to hardened hardware and virtual appliances, container-based delivery models, and can be embedded into select switches and routers. System dashboards allow for status checks at each site, reducing the risk of user error during deploying and facilitating ease of maintenance.
Most Security Operations Centers (SOC)are overwhelmed with alerts that necessarily consumes hours of investigation or pose little to no risk to the enterprise. CTD version 3.5 leverages artificial intelligence to improve both the user experience and security. CTD's five detection engines each generate different baselines of events and the system's ML Alert Algorithm correlates these events with other online patterns and behaviors on the network. While every change is logged in the system and classified as an event, only the highest fidelity alerts are delivered to the end-user for further review and investigation.
These alerts are integrated with Claroty Threat Intelligence and include the full context afforded by Claroty’s Root Cause Analytics. Risk-based indicators and a proprietary scoring index prioritize these ML-generated alerts within a user's queue and alerting sensitivities are entirely customizable to accommodate different organizations’ risk appetites.
Press Release: Claroty Extends Visibility of Market-Leading Industrial Cybersecurity Platform to the Internet of Things

