

Open-source software provider Red Hat has released the 2023 edition of their “State of Kubernetes Security” report that shows a cybersecurity investment gap for Kubernetes Solutions. The data, taken from an annual survey, with around 600 DevOps, engineering, and security professional respondents, shows that cybersecurity investment is lagging despite increased adoption rates for Kubernetes solutions.
Virtualization technologies, such as Kubernetes, have traditionally dwelled in the IT realm but are increasingly being deployed in industrial settings as IT and OT spaces continue to converge. Kubernetes provides a scalable and flexible platform for managing containerized applications, which encapsulates software and its dependencies within isolated units that can run consistently across different computing environments.
Increased flexibility, reliability, and agility are the primary drivers for adoption of cloud-native technologies, like containers, but security concerns are hindering these advantages. According to the survey, 67% of users had to delay application deployment due to cybersecurity issues, and 37% reported tangible revenue loss due to a cybersecurity incident.
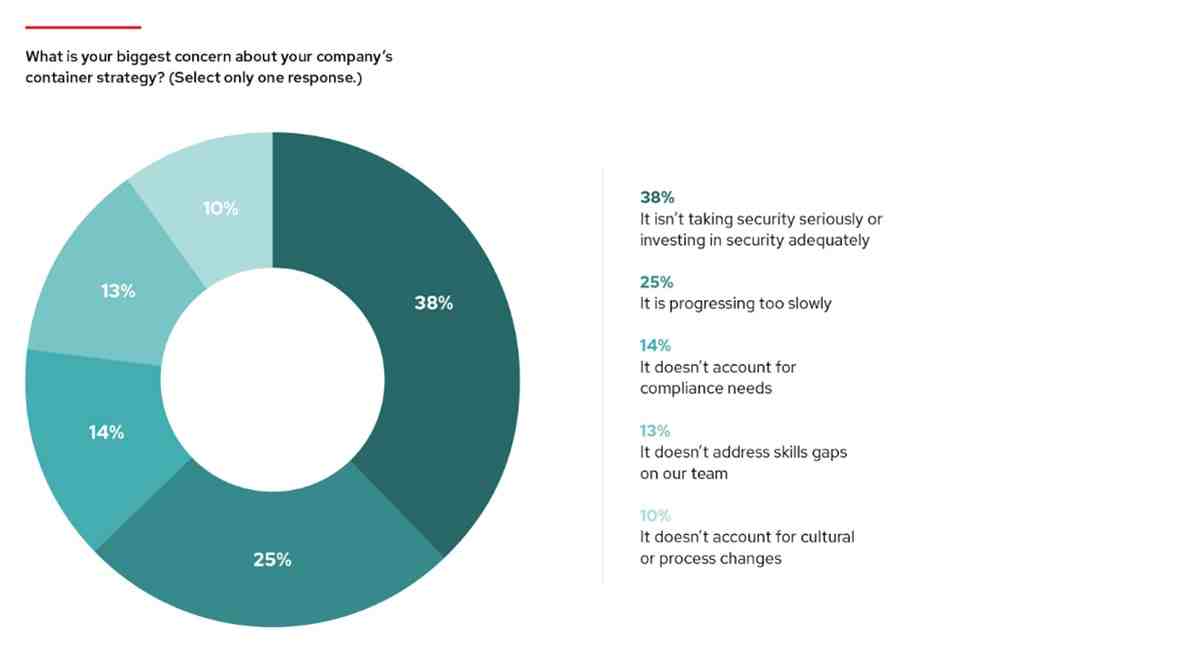
Despite this widespread concern, more than a third of survey respondents reported that their company was not adequately investing in securing its containerized workloads.
So how can enterprises make their containerized workloads more secure? Red Hat offers three suggestions:
Read the Red Hat Kubernetes security report State of Kubernetes security report 2023 (redhat.com)

