

Siemens participated as a Global Sponsor at ARC Advisory Group’s 21st India Forum titled Driving Sustainability, Energy Transition, and Performance through Digitalization on July 12th and 13th, 2023. With a turnout of over 300+ delegates the Forum provided a platform to network and disseminate information about new technologies and best practices.
In the session on Advanced Automation Enhancing Operational Excellence, Vivek Roy, Head - Digital Connectivity & Power, Process Automation, Digital industries, Siemens Limited spoke about the increasing importance of cybersecurity in digital enterprises with emphasis on circumventing the challenges of OT cybersecurity in legacy systems. He quoted Gene Spafford, a renowned Professor of Computer Science from Purdue, who said that even if a system is powered off, cast in concrete and sealed in a lead-lined room with armed guards he will still have doubts about its security. The best systems may be in place, but the vulnerability may come through a different attack surface. While this blog captures the salient points of Vivek’s presentation, it can be viewed in its entirety here.
Speaking about global megatrends, Vivek said that Covid -19 taught us a lot of lessons and catalyzed change in the manufacturing space.
The four global megatrends and their challenges are:
Digitalization: It is now a prerogative and with the increasing amount of data and connected devices the threat of IT/OT cyberattack surfaces are going very close to manufacturing.
Lack of skilled workforce: There are many specific skills needed for this area and this knowledge needs to be constantly updated.
Increasing legal regulations: More security guidelines and regulations are coming in. India has its own CERT (Computer Emergency Response Team) that is also enforcing guidelines that industries have to follow.
Globalization: It began with IT protection as that is the entry and exit point for data and OT security was lagging. But now OT security is catching up. Organizations must ensure remote work independent of the location and ensure secure data exchange between and within companies.
Today, everything is connected and therefore at cyber risk. Companies mostly secure the IT, and OT is not properly secured. The OT environment has different challenges and different security requirements. A very important aspect to consider is legacy systems. IT assets such as computers can be changed every 3-4 years, whereas OT assets continue being used for decades. “So, whatever is done in terms of cybersecurity in the IT space cannot be done in the OT space,” said Vivek. Statistics reveal that 72 percent of ransomware attacks occur in manufacturing.
The OT security journey comprises of six phases: awareness of a breach, outreach/asset discovery/network topology mapping, Oh wow! moment, firefighting, integration, and optimization.
Today, organizations cannot survive without connected devices; but connectivity increases vulnerabilities. Siemens has 740,000 connected devices globally out of which 13 percent of all vulnerabilities disclosed were critical.
A survey revealed that 91 percent believe that IT and OT should be collectively responsible for the security of machinery. Clients need help with OT security services and solutions. Reasons why OT security is still inadequate:
Asset lifecycle (do not refresh or patch assets)
Heterogeneity (too many OEMs, suppliers and technologies)
Focus on availability
Risk-based protection
Different cybersecurity legislations are underway in many parts of the world. In this context, Vivek spoke about the NIS2 directive tightening cybersecurity obligations across Europe. The focus is on new rules and more sectors are included. India is soon going to adopt the NIS2 guidelines. Organizations that don’t comply will be penalized.
Cyberattack causes downtime resulting in loss of production and intellectual property. For example, in a pharma company if a formulation is being done in a batch and there’s a ransomware attack the data is compromised. Money may help retrieve the data, but you must remember that it’s already in the dark web and you’ve lost the intellectual property to the process. That is why it is essential to have a comprehensive cybersecurity program.
Supply chain cybersecurity. When systems are purchased from OEMs/multiple vendors vulnerabilities can creep in. The customer thinks he’s buying the best-in-class, but even if one system integrator did not follow a guideline a new attack surface will emerge. That’s why you need to have cybersecurity specifications in your RFPs (Request for Proposals) and align with the right partner.
What is needed is a multi-layered cybersecurity concept based on the defense in depth principle for effective protection. This concept should cover the following aspects: data, systems, and people. Further, Vivek spoke about vulnerability management and keeping products secure through the entire product lifecycle with Siemens’ solutions. Next, he showed a chart that highlighted Siemens’ multi-layered defense in depth concept that covers three aspects: plant security, network security, and system integrity.
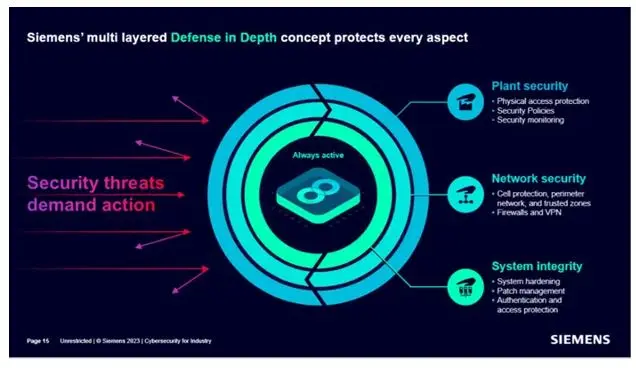
Speaking about the perimeter IT/OT integration network security, Vivek explained that even if OT gets attacked it should not affect the IT and vice versa. So both the islands need to be secured with very thorough endpoint protection and a risk-based approach.
The cybersecurity journey can be divided into five phases:
Where do I stand and where do I want to go?
Where do I start and which are my critical assets?
How can I protect my critical assets and secure my overall environment?
How do I know if my security controls are working?
What do I do in case of a cyberattack?
Underlying all these phases is continuous improvement. Siemens, with its comprehensive cybersecurity portfolio and the required expertise and experience drives digitalization securely.

