

Cost-effective cybersecurity remains a pain point and challenge for industrial control system installations to make Cybersecurity Improvements. The more critical the plant or infrastructure operated by a control system, the greater resources and attention are 
Two quite promising software-defined networking (SDN) technologies recently applied in industrial control systems may deliver substantial improvements in the cybersecurity of both new and existing industrial control systems. The first of these techniques uses an SDN protocol, OpenFlow, to manage a network. The second uses Host Identity Protocol (HIP, RFC 7401) to create and manage a secure identity-based overlay network that serves the automation components and shields these from general visibility. Both SDN techniques have already been employed in actual industrial installations and products have been released to the industrial market using both SDN techniques. Either might well be the most promising forward step for industrial cybersecurity since the invention of the firewall.
The first technique uses the OpenFlow protocol to lock down an industrial network. OpenFlow is a single protocol that replaces the plethora of existing routing and access protocols embedded in Ethernet switches. In an OpenFlow installation, the packet forwarding rules for an entire network of switches are managed from a central SDN controller. This separation of network control from packet forwarding enables more sophisticated and dynamic traffic management. Cognoscenti refer to this property as the “separation of the control plane from the data plane” (see figure).
The OpenFlow protocol has typically been used in large enterprise networks (for example, Google uses OpenFlow internally) and in large data centers, where OpenFlow is used to improve performance, especially as data center loadings change from hour to hour.
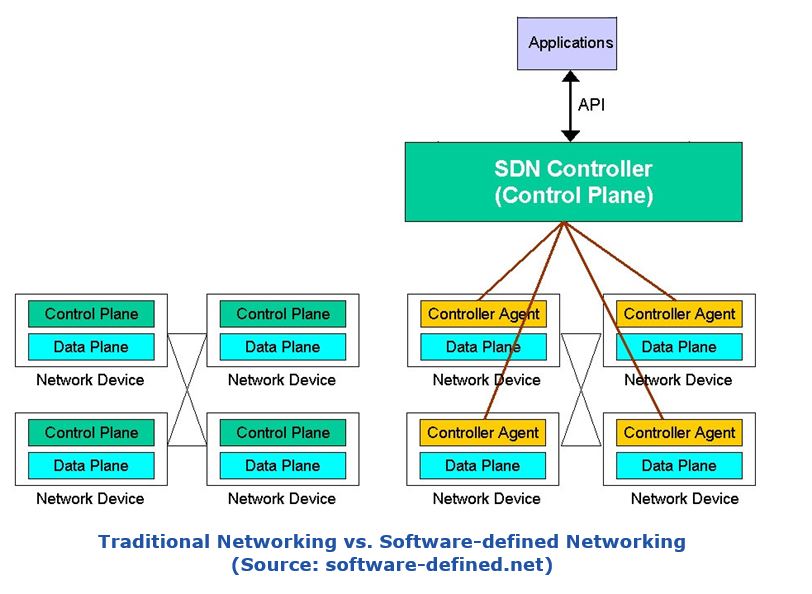
However, in industrial applications, practitioners report to ARC that the same protocol can be used as an effective way to lock down a (much smaller) industrial network or even part of an industrial network. The packet forwarding rules can be clearly specified and packets that do not match the rules can be forwarded directly to the network controller. The network controller is thus immediately aware of any abnormal network traffic and can restrict the network to forwarding only known packet types along pre-defined routes. In many cases this is a very suitable security solution for industrial automation networks, since their traffic often consists of a well-defined set of packet types and routes.
The first product example of OpenFlow as an industrial network security technique comes from Schweitzer Engineering Laboratories (SEL), a firm well-known for intelligent protective relays, substation automation equipment, and infrastructure for electric power transmission and distribution. In late 2016, SEL introduced an OpenFlow-based flow controller and an SDN configuration for some models of its industrial Ethernet switches, which are typically used in electric power substation automation. The network traffic within a substation consists of a relatively small number of message types and a small number of redundant network paths. The flow controller assigns rules to the network switches that enforce the desired path redundancies and require that all non-conforming packets be forwarded immediately to the network controller.
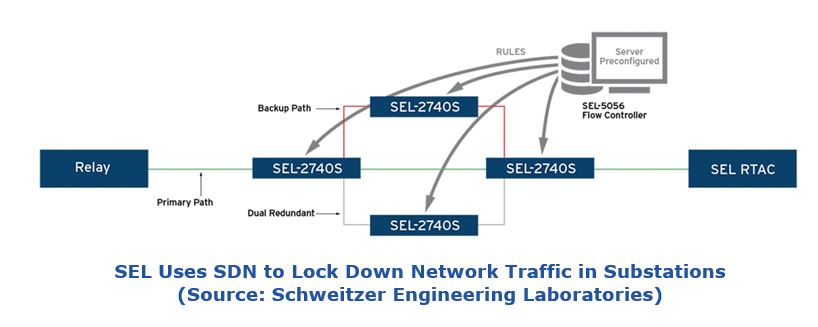
The network controller can also dynamically create rules that enable engineering access to the automation equipment and the protective relays located in the substation. Engineers report that the biggest advantage of their SDN network is the ability to lock down the substation network and immediately become aware of any packets entering the network that do not match the expected packet types and routes.
Major substations and other electric power T&D infrastructure are high-value targets for cyber warfare. They are critical for power system operation, so improvements in the overall security of networks within electric power substations represent an important security advance in the electric power T&D industry.
A second similar industrial example of OpenFlow has been announced by Yokogawa for several paper mills in Japan owned by the Oji Group. In this case, the networks secured were those linking the enterprise with the mills. These enterprise-to-plant paths can represent a significant risk, in that any compromise of the enterprise network may provide access to the process control networks within each paper mill. The general practice in industry is to provide extensive firewalls and other defenses to secure the plant networks so that traffic from the enterprise to the plant is extremely limited. This provides a high degree of security, but the restrictions imposed can cause difficulties for legitimate enterprise applications and for remote support of the plant manufacturing operations. They also require significant technical expertise to deploy and maintain.
The third example of enhanced industrial network security uses a very different strategy, which is a more radical departure. In fact, this strategy represents a break from decades of IP networking practice. The fundamental idea is to decouple the IP address from packet forwarding rules. Instead, network services are authorized and delivered based on secure identities.
The early days of the domain name system applications could reach virtually any point in the global internet by using its domain name or IP address. While this property of universal accessibility was very handy for applications such as web browsing, the ability to reach any point in a network is not necessarily an asset in industrial automation and is certainly not an asset in terms of industrial network security.
In place of IP addresses, a newer protocol (HIP) establishes secured identities among sets of devices. The network switches (which are all in a set of secure identified devices) provide services based on these identities rather than IP addresses. The overlay network traffic flows as encrypted IP payloads over the existing IP network.
What is an overlay network? The first historical examples date from the 1990s when the World Wide Web and its network traffic volume exploded. To maintain Internet performance, network operators developed overlay networks (now called Content Delivery Networks, or CDNs). These CDNs provided local proxy services in multiple locations, so that the overall point-to-point performance of internet websites remained acceptable to users regardless of their location. The overlay network they formed was invisible to casual web users. The firm Akamai grew out of this application and remains a leader in the field of CDNs.
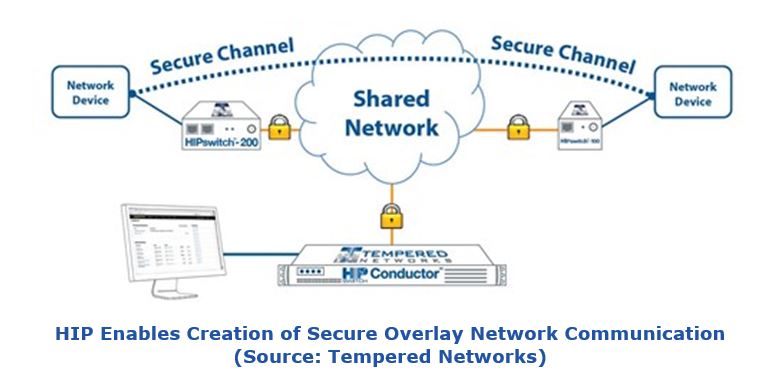
A secure overlay network, on the other hand, is not used to improve network performance but to deliver enhanced network security. The overlay network uses secure host identities rather than IP addressing to route packets on the overlay network. Secure identities takes the place of normal IP addressing for packet forwarding, though the overlay traffic is encapsulated in IP datagrams. Security is provided for the overlay network via HIP. Only devices possessing secure identities may join the overlay. The interesting part of this application is that it allows the network infrastructure to protect existing edge devices without any need to upgrade them. The network infrastructure can “whitelist” services for the end devices directly connected to it. These devices can continue to use their IP addressing but be permitted to join the overlay network, though remaining unaware of it. They communicate with the new smarter infrastructure, which passes their IP traffic via the secure overlay network.
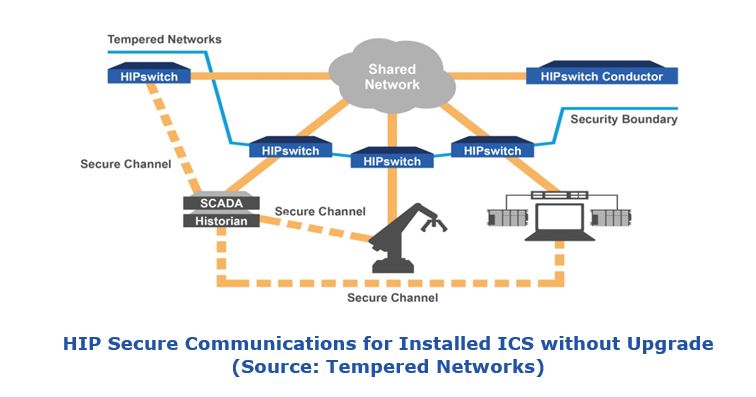
One very large manufacturer in the US (that requests anonymity) now uses this HIP strategy extensively in its largest plant, using equipment provided by venture firm Tempered Networks. One useful feature of this network strategy is that it can make industrial control system equipment invisible and unreachable except via the secure overlay network. It also enables segregation of control and information traffic. It enhances network security by limiting the freedom of packet flow on the network. The rules that define permissible network routes within the secure overlay network, and the rules defining the treatment of “legacy” IP end devices are highly flexible and can be managed from a single point.
Another benefit of a network based on secure identity is easier support for mobility and remote access. By extending the identity-based overlay network to mobile devices and remote locations, in-plant mobility and remote servicing can be accommodated without deploying VPNs. This could alleviate the difficulties end users experience in both these areas.

In this era of industrial cyber threats (and for these applications) both SDN techniques are excellent fits and they represent substantial improvement over what is typically installed in plant networks today. Critical infrastructure protection is a hugely important global concern. Here we have seen two ways in which forward-thinking suppliers are delivering greater security for critical infrastructure, and doing it today. Perhaps the largest advantage these technologies offer is that the industrial end devices (I/O systems, IEDs, PLCs, etc.) do not need to be upgraded to support the new cyber-secure network capabilities. Rather than upgrade the entire installed complement of industrial end devices (literally impossible in most plants) the network infrastructure can be upgraded instead to deliver higher levels of security.
Automation suppliers and industrial infrastructure suppliers can move their offerings in these directions now. The underlying technology is available. Why haven't all such suppliers done this already? End users should be asking their incumbent automation and network infrastructure suppliers what design choices they are making and when they will be delivering such new SDN technologies, which are providing enhanced industrial cybersecurity and network manageability in real industrial applications, and doing it today.
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Critical Infrastructure, Cybersecurity, OpenFlow, SDN, Security, SEL, Software-defined Networks, Tempered Networks, ARC Advisory Group.

