

Ensuring the cybersecurity of industrial control systems (ICS) has been an area of considerable attention for almost twenty years. This has been driven largely by the extensive use of these systems in various sectors of the critical infrastructure. Compromise of the control systems can lead to serious consequences, ranging from loss of production to equipment failure, threats to safety or environmental incidents.
Asset owners and service suppliers are taking the necessary steps to protect existing installed systems using mitigating measures ranging from improved processes, training, and technology. At the same time, suppliers must also ensure that their products are secure by design. Standards and certification programs have emerged to meet the latter imperative.
There is now a considerable body of knowledge on industrial cybersecurity. This consists of frameworks, standards, practices, and guidelines. The NIST Cybersecurity Framework describes a systematic approach to securing existing and installed systems, referencing a wide variety of standards and guidance documents for more detailed requirements. These references include NIST special publications 800-53 and 800-82, sector-specific standards such as NERC CIP, and cross-sector standards like ISA/IEC 62443.
Lack of relevant information is no longer a major issue. It could be argued that asset owners or end users are now overwhelmed by the quantity of available guidance and direction, leading to confusion and uncertainty about the best sources for a specific application.
Many of the standards and guidelines available concentrate on the actions system integrators and asset owners should take to protect existing systems. These tend to emphasize subjects such as asset identification and characterization, risk assessment, patch management, and compensating controls. These tools support a risk-based approach to securing installed systems through their lifecycle.
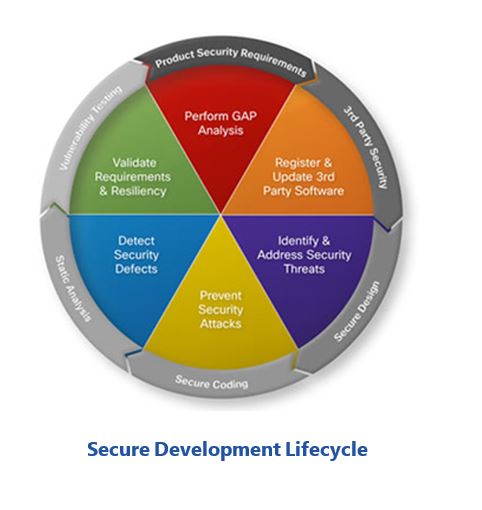
Long-term success will only be possible if product suppliers include security features in their products and use a secure development lifecycle. Emphasizing security during product development is certainly not new. Many if not most system and application software providers include security as an essential component of their development processes. The term “secure development lifecycle (SDL)” has become a common industry concept. There are various interpretations of the term across industries and most include the same basic security phases and activities.
To achieve the required results, security must be considered in all phases of development, including requirements definition, design, test, re-lease and support. Most industrial control systems’ suppliers recognize this and have taken steps to improve the intrinsic security of their products. Some have implemented secure development practices similar to those used by suppliers of enterprise and other types of software. This is encouraging, and asset owners should expect it from all suppliers. They should also clearly identify the features that products must have to improve their security performance.
While individual suppliers can certainly address these needs independently, it is far more effective and efficient to base the response on well-defined standards that can evolve to meet changing needs. This also contributes to consistency across suppliers.
The ISA99 committee and IEC Technical Committee 65 have developed and approved the 62443 series of international standards that address industrial automation and control systems (IACS) cybersecurity. Collectively, these standards provide requirements and guidance for all participants and stakeholders in the lifecycle of IACS, including component and system suppliers, system integrators, asset owners, and service providers. This lifecycle begins with the development of single components, such as an embedded controller, or a group of components working together as a system or subsystem.
Two of the recently published standards in the 62443 series focus primarily on product development. Although directed primarily at product suppliers, these standards are also useful references for asset owners for use in product selection.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information on how to become a client, please Contact Us
Keywords: Design, Development, Lifecycle, Maturity, Secure by Design, ICS, ARC Advisory Group.

