

Remote access to operational technology (OT) assets offers significant benefits for industrial companies. Remote access reduces the resources needed for operations staffs to monitor and control geographically distributed assets. Maintenance teams can reduce downtime with remote asset monitoring and, if needed, rapid response by off-site personnel and vendor experts. Engineers can continuously monitor and improve operating practices. And with remote access to OT assets, experts in IT and security operational centers (SOCs) can help plants reduce the likelihood and impact of cyber incidents.

Executives from Owl Cyber Defense recently briefed ARC Advisory Group on what that company is doing to address this critical issue. The company’s new ReCon product is a security-hardened, data diode-based network isolation device specifically designed to address the specific challenges of secure, bi-directional access to OT systems.
The security of operating facilities is a critical concern for every industrial company. A compromised control system can have devastating consequences for the health and safety of workers, the environment, critical equipment, and operational performance. The financial and reputational impacts of a serious incident could jeopardize a company’s very survival.

Recognizing this situation, regulators and standards bodies have developed various guidelines for secure remote access. Most are based on proven IT best practices with adjustments for control system concerns and constraints. While use of these recommendations won’t achieve the absolute security that air-gaps can, they can substantially reduce cyber risks. Typical guidelines address:
Selecting the right boundary protection device is one of the most important decisions as these devices control the flow of information into the OT systems. Some of these devices can also be used to control user access to individual OT devices and the activities performed. Boundary protection devices include gateways and conventional software-based firewalls, next-generation firewalls (NGFW), industrial deep packet inspection (DPI) firewalls, and data diodes. The best device depends on a variety of factors including the facility’s cyber risk tolerance, OT security architecture, and the use cases that need to be supported.
Where possible, users should include other security controls in their bi-directional use of any of these devices to increase the facility’s defense-in-depth protection:
Established in 1999, Owl Cyber Defense is a US-owned and operated company headquartered in Danbury, CT. Owl is a global supplier of data diode and cross domain network cybersecurity solutions. With a focus on customers in the military, government, critical infrastructure, and commercial communities, Owl develops one-way data cybersecurity solutions to address a wide variety of industry pain points, technologies, and best practices. The company has helped hundreds of organizations around the world secure their networks.
The Owl commercial product line focuses on the needs of critical infrastructure operators. These cybersecurity products protect data networks and digital assets (SCADA, PLCs, DCS, databases, historians, etc.) within critical infrastructure facilities like plants, mines, power plants, substations, pump stations, and oil rigs.
Solutions are available with a range of software interfaces that support the transfer of files, alarms, logs, events, streaming video, database data, and historian information, from a variety of popular OT product providers (i.e. GE, OSIsoft, Rockwell Automation, Schneider Electric). Data transfers can be single events, small files, extremely large files, or the replication of a whole database/historian. Owl supports speeds from 3 Mbps to 10 Gbps in a variety of form factors (e.g. enterprise server-based card kits, 1U rack-mount enclosures, and DIN-rail models).
ReCon, a recent addition to Owl’s critical infrastructure product portfolio, supports the need for secure, bi-directional access to industrial control systems. This solution contains a variety of unique features for controlled transfer of messages between external users and plant applications. According to the company, this provides greater security assurance than a conventional firewall. The design reflects Owl’s deep experience in boundary protection solutions for a variety of unique high security challenges.

ReCon uses two one-way data diode paths to help ensure isolation. These paths are completely independent in operation and control. Independently managed source and destination proxies provide the features needed to effect bi-directional communications.
The following figure illustrates how the ReCon boundary protection device can help address the requirement for secure remote access.
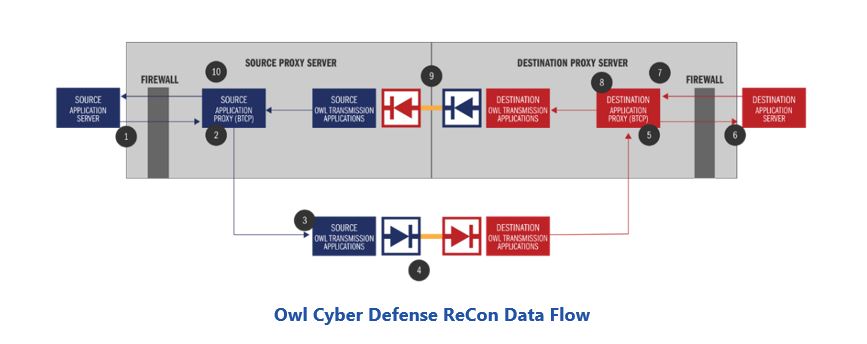
During operation, these steps isolate source and destination sides functionally and physically and ensure that only pre-defined messages can cross the security barrier. ReCon also provides separate ports and configuration pages for the individual sides of the device, as well as separate administration ports with independent logins. This can help prevent the possibility that an external user might modify the allowed communication patterns.
Enabling external access to plant assets is becoming mandatory across the industrial landscape. Security teams need to accept this fact and develop strategies to address the additional cyber risks. Data mapping and file exchanges through one-way boundary devices provide the best protection if the only need is to share OT-related data. Bi-directional exchanges require a comprehensive secure remote access strategy to manage the amplified cyber risks. These strategies should incorporate guidance from regulators and standards 
As this report discussed, things can be done to improve the security of bi-directional communication devices. Dedicated cybersecurity products such as the Owl Cyber Defense ReCon product, which reflects that company’s deep expertise in developing high security products for use in military, intelligence, and critical infrastructure, can certainly help. ARC recommends that industrial companies consider how use of these kinds of products might improve the security of their facilities to enable the many benefits of today’s digital transformation initiatives.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Secure Remote Access, Digital Transformation, Industrial Cybersecurity, ARC Advisory Group.

