

The following is a guest blog post from Melissa Cowin, marketing manager of Fybr, an end to end IoT smart city solutions provider. Fybr has their own blog that’s worth checking out and you can see Melissa’s other posts here.
The growing number of ransomware attacks on state and local government means cybersecurity is a crucial consideration for Smart Cities today. Additionally, the millions of connected IoT devices in Smart Cities could potentially leave a city vulnerable to hackers. Ponemon Institute, a Traverse City, Michigan, research company estimated that 38% of public entities it sampled suffered a ransomware attack last year. That number was a 13% increase from 2016 indicating the cyber-attack trend continues on the rise. A study recently published by Allan Liska (Recorded Future) revealed there have been over 169 reported cases of successful ransomware attacks on state and local governments since 2013. The study showed a decrease in the number of attacks from 2017, but a large increase in 2018, and an upward trend for 2019. The report stated that there have already been 23 reported cases this year. It is important to note that the study indicates that not all cases of ransomware attacks are publicly reported so the number is most likely much higher. Unfortunately, ransomware is a big issue that many cities lack funding to address and it is not going away any time soon.
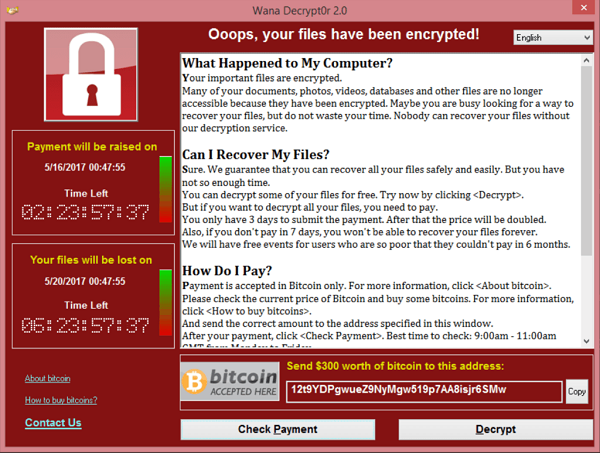
In all cases of targeted attacks, the targeted city is left with a big problem, halting productivity across its departments that severely restricts the cities’ ability to serve its citizens. It is misleading to hear the term ‘targeted attack’ because most cyber terrorists are not targeting specific cities; instead, they look for vulnerabilities and attack where it is convenient and easy. Once they realize they are dealing with a state or local government they leverage their position to hold them hostage, demanding payment in cryptocurrency to restore their access to important data or files.
This is an issue that cities will need to take a proactive versus reactive approach to. The following are some questions and answers to help guide state and local government on how they can address cyber-attacks by understanding what ransomware is, whether or not they should pay a ransom, and how to take a proactive approach to cybersecurity to mitigate the risk of cyber terrorism.
\Ransomware is malicious software (malware) that uses encryption to hold data/files for ransom. Most of the time the attacker will request payment in the form of cryptocurrency with the promise to provide an encryption key to regain access. Hackers have become more sophisticated with cryptography and are creating new techniques and tactics to stay fresh and effective. Norton has identified 5 types of ransomware:
There is a wide variety of malware today and these programs continue to evolve. Some of the better well-known types include SamSam, CryptoLocker, WannaCry, and RobinHood. They are effective because they halt a city’s ability to provide critical services to its citizens, not paying a ransom can still cost the city millions of dollars, and they threaten to disrupt and erode public confidence in the government.
In May of this year the city of Baltimore, Maryland was hit by ransomware. Smart Cities Dive reported that the FBI identified the ransomware to be a “fairly new variant” of RobinHood stating that it is “quite aggressive”. The effects of the attack left the city unable to access email and accept credit card payments for permitting. This is the second attack on Baltimore within 14 months and details are still coming out about how the system became infected and where the vulnerabilities were.
\Every victim of a ransomware attack asks, “Should we pay the ransom?” The costs associated with an attack can become extremely high, whether you pay a ransom or not. Authorities and cybersecurity experts generally recommend not paying the ransom because there is no guarantee that the encryption key will even work. State and local governments are left with a more troubling situation of the costs that go beyond the attack. They have to either pay employees for the time it takes to clean up the corrupted system or hire experts to do the job. They have to invest even more capital into implementing new security software or build an entirely new system to protect themselves now and in the future.
Atlanta, Georgia is one example that illustrates how much an attack can cost. The ransom demanded equated to approximately $51,000 (note they demanded payment in cryptocurrency). The actual cost to recover from the attack added up to approximately $17 million (estimate reported by the Atlanta Journal-Constitution). It may seem like paying the ransom is the less expensive option, but remember these cyber terrorists seek to extort their victims and paying the ransom may not result in the data/files being accessible or restored. Atlanta also had to take the necessary steps to ensure that their city is protected and prepared for future attacks.
Cities can be proactive in their approach to mitigating the risks of a cyber attack by planning and preparedness (data governance), investigating thoroughly new technology and devices (including IoT sensors) to ensure they are secure, share threat information and solutions with other state and local governments, and purchase cybersecurity insurance to enhance resilience and improve cybersecurity around the world.
Fybr’s Principal Platform Engineer, Paul Becker, recommends some helpful cybersecurity tips:
“Cities should consider a multi-layered approach to cybersecurity. User education is essential to understand how systems get compromised and how to recognize threats. Antivirus systems must be installed and active. Adopt a password management system and use it - no weak passwords anywhere. Account permissions need to be restricted to what is required to do a job, nothing more. Systems must be patched with the latest updates. Everything should be backed up and those backups should be tested. Finally, a response plan should be in place to recognize a problem, isolate systems to contain the infection, remove the infection, and restore to working condition.”

