

Many industrial operations remain at risk of costly, disruptive cyber incidents. Despite their significant investments in defensive technologies, most companies don’t do a good job of maintaining them. This is often due to an imbalance between investments in security technologies and the people, processes, and security management technologies needed to sustain them.

ARC Advisory Group analysts recently discussed the current state of industrial cybersecurity with PAS Global executives. The company’s Cyber Integrity solution was developed to help industrial companies overcome major obstacles to effective maintenance of control system cybersecurity. Features include automation of critical activities like asset inventory and vulnerability management, automatic detection of endpoint changes, and risk analytics for situation awareness and program management.
ARC’s research across a wide spectrum of industrial companies consistently shows that many industrial companies struggle to derive value from sophisticated cybersecurity technology investments. Lack of appropriate people, processes, and security management technology has undermined the effectiveness of security investments. Unaware managers continue to operate with a false sense-of-security.
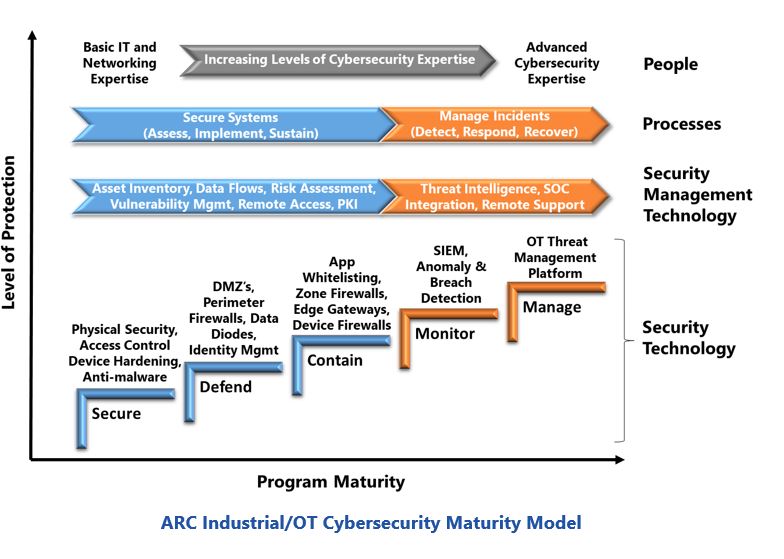
ARC developed its Industrial/OT Cybersecurity Maturity Model to help companies implement effective cybersecurity programs. The model provides a roadmap for building sustainable layers of defense through incremental investments in security technology, security management technology, processes, and people. Satisfying requirements at each step ensures that the organization is prepared to advance to the next maturity level. The colors in each step distinguishes defensive measures used to minimize the likelihood of a system compromise from those needed to detect and respond rapidly to sophisticated attacks.
Security management technologies are an essential, but often overlooked, part of ARC’s model. As most companies have a shortage of cybersecurity resources, optimizing productivity is essential. Security management technologies support this goal through automated security management workflows, enhanced visibility of critical risks, and ready access to information defenders’ need for rapid response to sophisticated attacks.
PAS Global designed its Cyber Integrity security management technology solution to help improve the efficiency and effectiveness of people responsible for maintaining plant security. The solution’s capabilities support execution of critical tasks in the Secure Systems and Incident Management processes in ARC’s model. This includes functionality for: developing and maintaining asset inventories; identifying, evaluating, and managing system vulnerabilities; detecting and managing unexpected system changes; and, analyzing and visualizing system security risks.
Lack of a trustworthy, up-to-date asset inventory is a major problem in most plants, especially those with legacy systems. Manual efforts to address this situation often fail because of the costs and downtime requirements of plant walk downs. When walk downs are performed, unrecorded changes to hardware and software still erode information quality. Automation is the only answer for this critical activity.

Many products are available to build and maintain accurate inventories for conventional IT cyber assets (level 2 and above), but these are not adequate for industrial control systems. IT-centric solutions don’t collect the deep, proprietary, configuration data needed for security management of critical control system elements. These include DCSs, PLCs, and safety systems.
PAS Global Cyber Integrity automates the collection and management of information for all control system assets, from level 0 through level 3. This includes detailed configuration data on I/O cards, control strategies, installed software, and firmware for all major control systems, regardless of vendor. When combined with the information it gathers from IT assets, it can provide companies with a single, complete asset data repository for security maintenance and incident management.
Cyber Integrity can collect this information from devices connected through TCP/IP, serial, and other methods used in control systems, as well as isolated and transient OT assets.
Plants need an effective vulnerability management program to achieve the security goals of the first three steps in ARC’s model. There is a continuous stream of vulnerability alerts for control system products and the security technology used to protect them. Promptly addressing these notices is essential to protect assets from cyber-attacks.
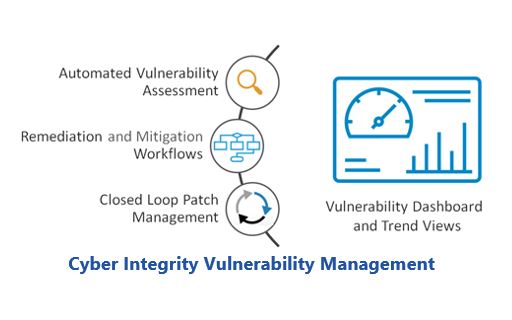
Cyber Integrity provides extensive support for all these actions. This begins by automatically collecting vulnerability alerts listed in the US-CERT National Vulnerability Database (NVD). Relevance is evaluated using Cyber Integrity’s in-depth asset inventory and the affected hardware and software identified by plant, unit, area, zone, and individual ICS asset.
Cyber Integrity also provides support for managing the complex workflows required for remediation and mitigation. This includes documenting decisions and actions taken throughout the various stages of the patching process including patch acquisition, evaluation, testing, implementation, and verification.
While vulnerability management is essential, plants can still be at risk of safety, environmental and operational incidents related to cyber asset integrity. Sophisticated attackers can leverage other weaknesses like undocumented vulnerabilities (zero-days) and stolen credentials to overcome defenses. Staff members can also make configuration changes to OT assets that inadvertently create unsafe conditions. Rapid detection of these situations is essential to minimize the impact.
These situations require continuous monitoring of all assets for unexpected changes. While many companies are adopting anomaly and breach detection technology for this purpose, these solutions only detect anomalies in network communication. Changes to the configuration and programming in proprietary control system assets can still go undetected. As these devices have direct control over the process, these compromises represent the most significant risks for industrial plants.
Cyber Integrity addresses the issue directly and comprehensively with periodic assessment of all assets for changes to configuration, control strategies, graphic files, and logical files. The asset inventory provides the basis for detecting changes and the solution issues alerts of any suspicious situations with actionable context.
Identifying at-risk cyber assets, understanding their role in the process, and visualizing how risks can propagate is critically important for effective security defense maintenance and incident management.
Cyber Integrity’s Risk Analytics supports this need through a topological view showing all assets and system connectivity relationships. Current risk levels, based on NVD (National Vulnerability Database) score and an asset’s role, are indicated for each asset and end users can easily see how an attack might propagate to other assets. For example, they can visualize how an attacker can use a compromised asset, such as an engineering workstation, to pivot through the OT environment and put critical assets, such as the DCSs and SISs, at risk.
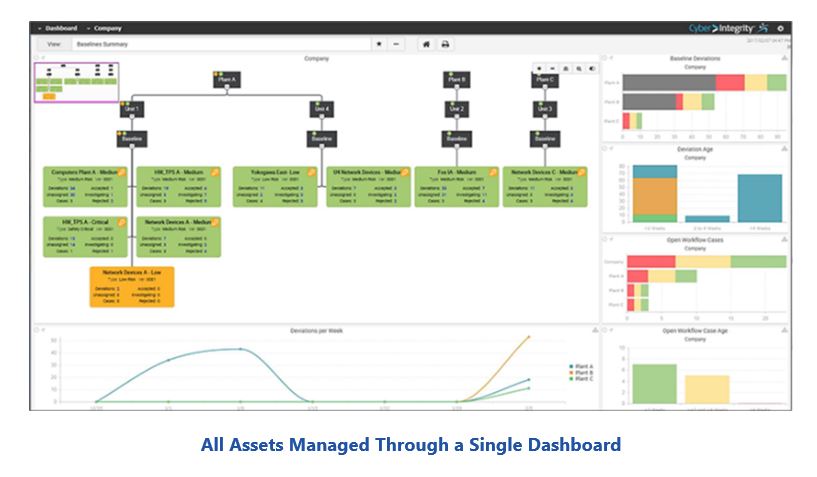
Cyber Integrity Risk Analytics can help managers maintain awareness of plant security risks. Likewise, it can help security teams direct and monitor critical security management activities. Users can also drill down from the topological map to view complete documentation for each asset. This includes current vulnerabilities, configuration information, and complete change histories.
Time is of the essence when an incident occurs in an industrial environment. Responders need quick access to complete system information to isolate, remediate, and restore operations. Often, IT and even OT teams believe mistakenly that level 1 and 0 systems are immune from compromise due to their proprietary nature. The reality is that these assets have been targeted and compromised. Malicious changes to configurations and programming can impact safety, environmental, and operational goals. Detecting and removing such changes is critically important.
Every industrial company needs a solid foundation of basic cybersecurity practices including asset inventories, vulnerability management, change detection, and risk visibility. Lack of resources prevent many companies from achieving this basic goal. Automating these activities by using appropriate security management technology is the best way to lessen the load. ARC recommends that all industrial companies consider software like Cyber Integrity as a foundational element of a defense-in-depth cybersecurity strategy.
ARC was impressed by the comprehensiveness of the solution from PAS Global, a company with a strong reputation within the control system community. According to the company, Cyber Integrity is a scalable, enterprise-class software solution built on the PAS Global Integrity platform, which is deployed at hundreds of sites across the world.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Industrial/OT Cybersecurity, Maturity Model, PAS Global, Cyber Integrity, ARC Advisory Group.

