

I was intrigued to read Sid Snitkin's recent blog, ARC’s Industrial Cybersecurity Maturity Model Evolves. What interested me is how in the five-step model each level of security (Secure, Defend, Contain, Monitor, and Manage) is built on the previous level. It makes sense. To start with, you need physical security of the devices and hardware. If they aren't secure, nothing else matters much. Then you need to defend them from outside attacks. Next, should an attacker penetrate the defense, you need to be able to contain the damage. And at the more advanced levels, monitoring and management come into play.
This model makes it clear that unless and until you've achieved some degree of security at a given level, it's going to cause problems further up the chain. For example, if you have an open firewall into your plant or process at the Defend level, the containment, monitoring, and management will have to work doubly hard to protect you. On the other hand, if you are able to keep all of your firewalls closed, it makes the work at the Contain, Monitor, and Manage levels so much easier.
Until recently, that's how it was. People didn't need to expend too much effort on security since it was relatively easy to keep firewalls closed. The plant network could be isolated—air-gapped if necessary—because there was little need for process data outside the plant. But times have changed. In the age of Industrial IoT, Industrie 4.0 and value-driven demand for IT/OT integration, remote support, and digital transformation, sealing up the plant is no longer an option. It has become increasingly necessary to access process data.
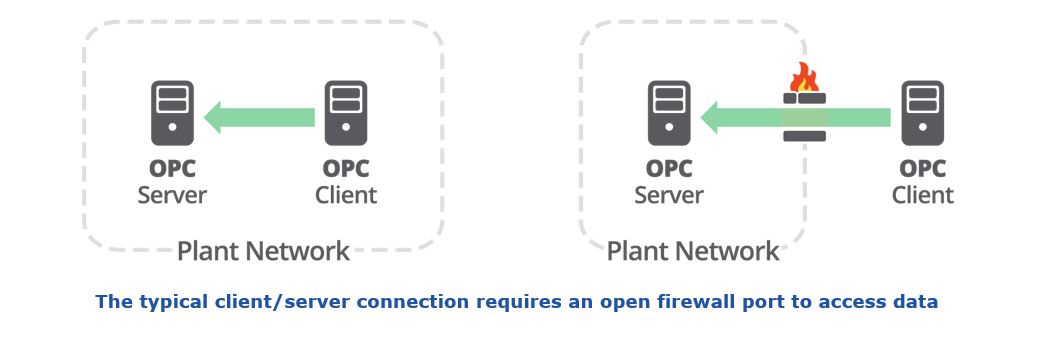
Here's where a fundamental problem appears. A typical industrial system provides data through client/server relationships. The client requests data from the server, and the server then sends the data to the client. When both are on the same network, behind the same firewall, all is fine. But when the client is outside the plant, it cannot connect to ask for data without opening a firewall. Most industrial data networking protocols, including OPC UA, work this way and have this problem.
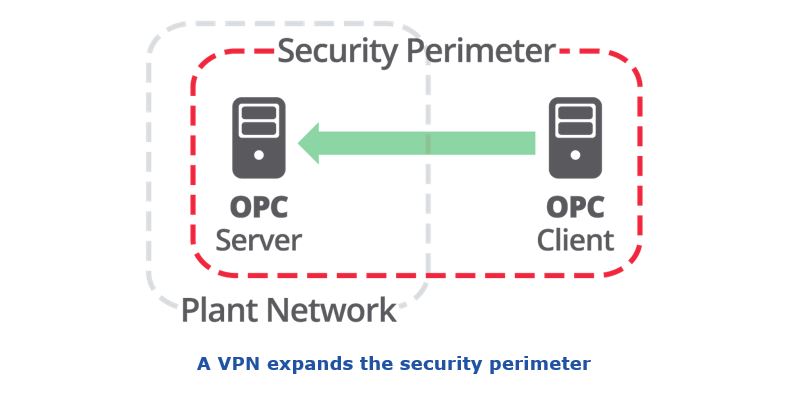
The most common work-around is to use a VPN. To some this may seem safe, almost as if you were bringing the client into the secure environment of the plant. But actually, it's the other way around. Using a VPN simply expands the security perimeter of the plant to include the client. Now the plant is exposed to whatever risks the client is exposed to. This is how the NSA EternalBlue exploit propagated the well-known WannaCry virus, and still remains a serious threat today.
A better solution is to make all plant connections outbound-only, which keeps all inbound firewall ports closed. This can be done using IoT middleware that connects to the server within the firewall, and then makes an outbound connection from the firewall to a similar IoT middleware component connected to a DMZ or directly to the client. To sustain robust industrial communication, the IoT middleware should support bi-directional, real-time data transfer at rates of tens of thousands of tag changes per second. And, it should fail gracefully and recover quickly from network outages. It should have no impact on the working system, allowing clients to access process data without accessing the network.
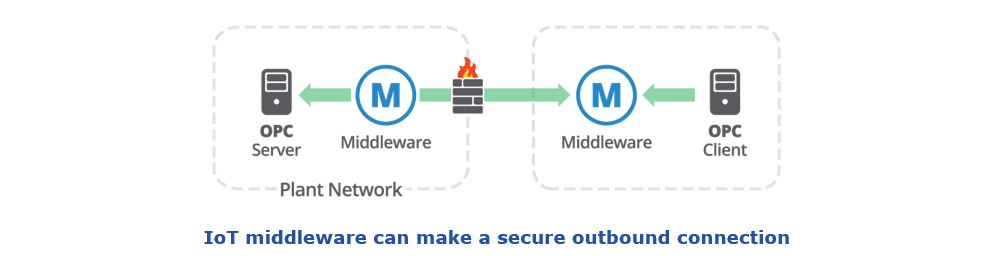
In addition to closing all inbound firewall ports, this technology can also be used for containing intrusions at zone firewalls, edge gateways, and device firewalls. When the system is secure, defended and contained, the monitoring and management will be much easier. It may not be quite as hands-off as it was in back in the old days when nobody had access to plant data, but it is just as secure. Maybe even more so.
Bob McIlvride is the Director of Communications at Skkynet Cloud Systems, Inc. Since 1999 Bob has served as Communications Manager at Cogent, responsible for writing and editing technical documentation and marketing communications, as well as managing sales and distribution channels. He received an MA in Professional Writing in 1986 and a BA in Natural Law (Interdisciplinary Science) in 1984 from Maharishi International University in Fairfield, Iowa, and has 15 years writing and publishing in the natural gas and process control industries.

