

The ISA/IEC 62443 series of standards includes fourteen individual documents, each addressing a specific aspect of the subject of industrial systems cybersecurity. The majority of these are standards, collectively providing a comprehensive set of normative requirements that apply across all phases of the solution life cycle, from specification and development through implementation to operation and support.
To make informed decisions about the design and operation of an industrial cybersecurity program it is first necessary to conduct a thorough risk assessment, addressing threats, vulnerability, and potential consequence. The results of this exercise are then used by the asset owner and operator to determine where to best apply scarce resources for the optimum result. Until recently there has been a dearth of practical guidance on how to conduct such an assessment. There are companies that provide this as a service, but it is also important that asset owners have guidance on how to perform assessments for themselves. Fortunately, the basic approach is similar to that used for safety assessments, a methodology long practiced by safety engineers. This has led to the emergence of concepts such as security process hazard analysis (PHA).
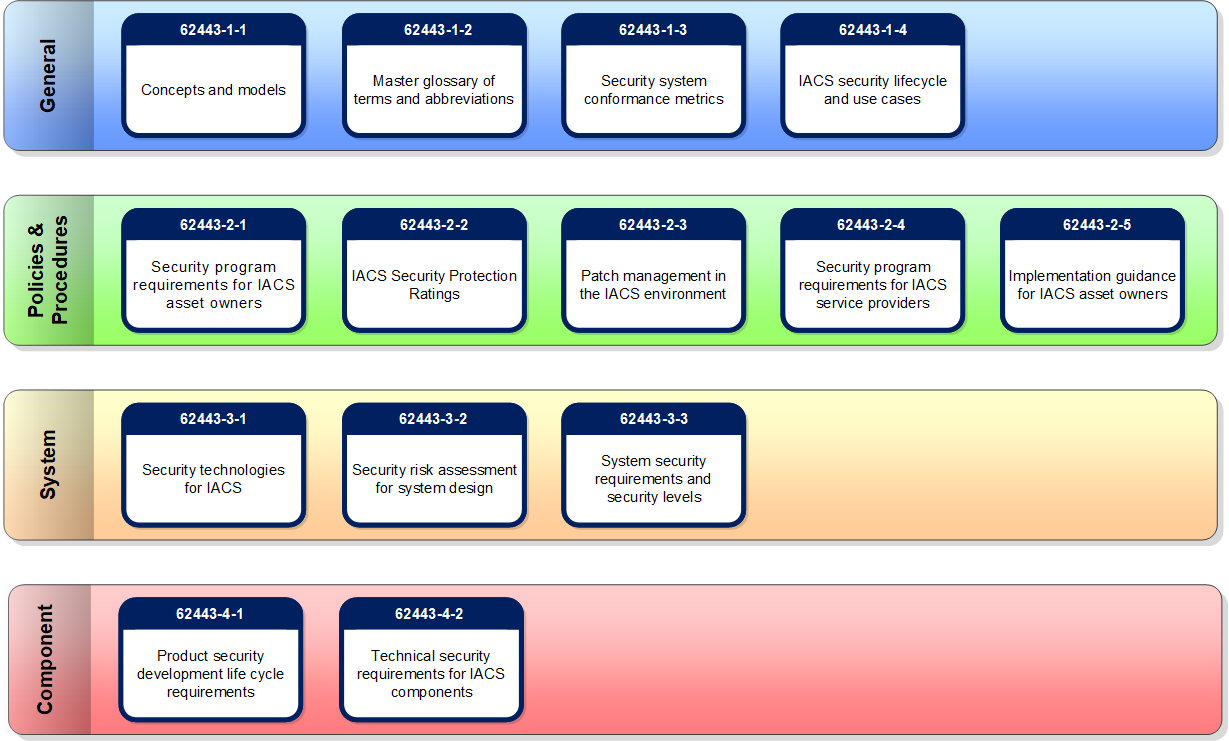
The ISA99 committee recently completed work on a standard to address this subject. Now available as IEC 62443-3-2 and soon to be available for purchase as ISA-62443-3-2, this standard defines a set of engineering measures that guide an organization through the process of assessing the risk of a particular industrial control system and identifying and applying security countermeasures to reduce the security risk to tolerable levels.
The intended audience includes asset owners, system integrators, product suppliers, service providers, and compliance authorities. The standard is organized around a comprehensive workflow that each of the following steps, as well as the required inputs and expected results.
1. Define a system under consideration (SUC).
2. Perform an initial risk assessment.
3. Partition the SUC into zones and conduits.
4. Determine whether the initial risk is tolerable.
5. Perform a more detailed risk assessment if required.
6. Document the security requirements, assumptions, and constraints.
Collectively there are over thirty normative requirements defined for this process, each with appropriate rationale and supplemental guidance.
ISA/IEC 62443-3-2 is a critical and long-anticipated component of an effective cybersecurity response and reflects accepted practices or several disciplines. Those with a need in this area or an interest in this subject are encouraged to learn more about it from service providers, training organizations, and other informed sources.

