

Managing the cybersecurity of industrial and infrastructure operations has never been more challenging. Major incidents have shown that sophisticated attackers can find weaknesses in conventional defenses and gain access to critical controllers and sensors. In response, companies must find ways to strengthen security posture and enable rapid detection and response strategies that can minimize the impact of a successful cyber compromise.
Digital transformation adds fuel to this fire. Consider the multitude of industrial IoT devices being deployed to support broader use of analytics and AI; to enable predictive maintenance and remote control; and, new business strategies like additive manufacturing. These deployments greatly expand the connectivity, 
A security weakness in an industrial IoT device is a threat to facility safety and operational continuity. In operational technology (OT), security concern often equals safety concern. Insecure industrial IoT devices are also a threat to any system connected to a facility, like corporate information technology (IT) systems. Security teams need to be as diligent in managing these security risks as they are in those related to plant equipment and business continuity. This includes ensuring that all industrial IoT devices are secure-by-design, integrity hardened, protected from external attacks, and monitored continuously for potential security compromises.
Recently, ARC Advisory Group discussed the challenges of managing industrial IoT device security with executives from Irdeto. Irdeto helps suppliers protect and monitor the security of industrial IoT devices and applications. A summary of the company’s products and services follows.
The security of industrial IoT devices is a major concern for end users and suppliers of industrial IoT devices. Insecure devices put the safety, environmental, and operational performance of every industrial company at risk. The financial liabilities, safety impacts, potential loss of intellectual property and reputation damage from a serious cyber incident ascribed to weak product security could bankrupt an industrial IoT device supplier.
To manage these risks, industrial IoT device security must be a shared responsibility. Suppliers must accept responsibility for providing devices that are secure-by-design, with defense-in-depth, and protected against compromise to operational and security integrity. End users must accept responsibility for securely installing and configuring devices and securing their connection to external systems and security monitoring systems. End users can generally meet their obligations by following standards like IEC-62443 and NERC CIP but must also look to the broader set of threat cases that may apply to each specific deployment. Suppliers need to ensure that industrial IoT products support these standards and development teams follow appropriate secure product development guidance.
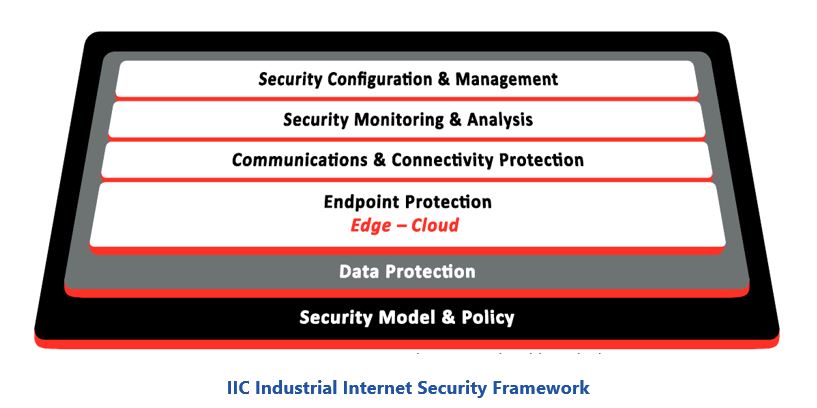
References such as Industrial Internet Consortium’s (IIC) Industrial Internet Security Framework provide a good baseline for building product security into devices. This framework addresses key issues like: endpoint protection; communications and connectivity protection; security monitoring and analysis; and, controlled security configuration management for all components of the system. While helpful, these guidelines can be overwhelming for suppliers lacking cybersecurity expertise, which is often the case given today’s extreme shortage of cybersecurity professionals. Cybersecurity requires special training not covered in traditional IT and engineering training programs. In such cases, ARC recommends use of experts in product security to review designs considering the potential threat landscape and associated defense-in-depth strategies.
Sustaining the operational and security integrity of devices is a separate, but equally important issue. Even a well-designed IoT device can be compromised if a sophisticated hacker gains access to the product’s software. Protecting software and all IP is essential throughout a product’s lifecycle and across the complex software supply chains that contribute to the code used in most devices today. With the sophistication of currently available hacker tools (such as IDA PRO), reverse engineering remains a threat that today’s secure coding methodologies or vulnerability scanners/static analysis tools can’t always solve. Security efforts should include protecting software in physical devices against reverse engineering. The low cost and wide availability of industrial IoT devices make them easy targets for hackers to reverse engineer critical code and uncover vulnerabilities that can be sold on the dark web. Software hardening, through techniques like obfuscation, and continuous monitoring of software integrity is the only defense against these kinds of security attacks.
Concern over the security of industrial IoT devices continues to constrain digital transformation efforts. To overcome this hurdle, users need to have confidence in the security of products and supplier processes. Compliance testing and independent third-party auditing can help suppliers demonstrate the adequacy of security processes and products.
Irdeto offers products and services that address the critical need to protect industrial IoT device software within devices and across the supply chain. Established in 1969, Irdeto has a strong background in protecting digital assets and business models in video entertainment and connected industries. As we learned, the company’s software protection technology and cyber services currently protect more than five billion devices and applications for some of the world’s best-known brands. This includes digital platforms and applications for video entertainment, video games, connected transport, and IoT-connected industries.
While the company has many products that developers can use to protect software distribution across supply chains, the ARC briefing focused on Cloakware technology, the company’s core offering for protecting software within industrial IoT devices. This offering includes technologies and expert services to help developers build appropriate defenses and protect software against reverse engineering, tampering, and automated attacks.
Irdeto designed Cloakware Software Protection (CSP), a suite of advanced technologies, libraries and tools, to enable companies to customize the protection of critical digital assets such as keys, code, and data. Cloakware’s security techniques protect applications through sophisticated data, function, and control flow transformations, anti-debug, whitebox cryptography, and active integrity verification. CSP integrates these security techniques into the customer’s software build process, thereby applying the protections to source and data transparently to the developer, and entangling the protections inseparably with the software. Key features of the Cloakware technology offerings include:
In other words, Cloakware Software Protection is designed to ensure that software, and its data, operate in the way that was intended by the original design.
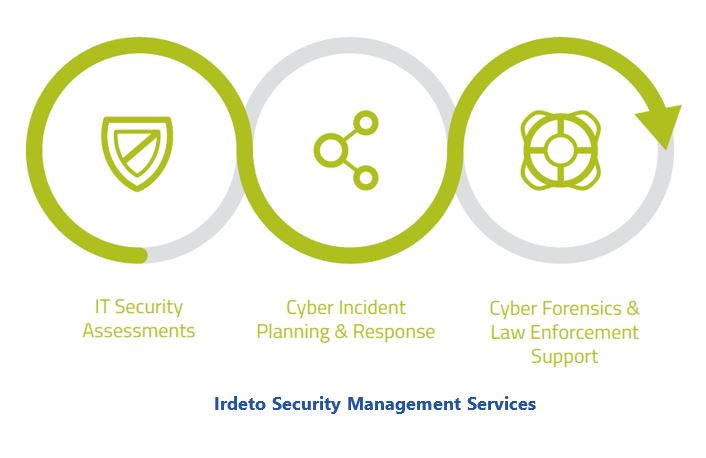
Irdeto believes that an appropriate industrial IoT device security strategy requires ongoing evaluation of potential security risks as well as planning for security iterations in product revisions. The goal should be to maintain a consistent net positive security position against hacking trends relative to competitors in the market. Accordingly, the company provides an ongoing program of security services. This includes:
Securing industrial IoT devices is essential to enable performance improvement in industrial and infrastructure operations. Ensuring security is a shared responsibility between the users and suppliers of industrial IoT devices. The chances for success can be greatly enhanced when all parties follow appropriate standards and guidance, followed up with thorough risk assessment of potential hacker motives against the IoT device and any system where it is used. Use of third-party experts can fill any gaps in cybersecurity expertise.
Many industrial IoT suppliers already provide devices equipped with the hardware and endpoint protection needed to help stop cyber-attacks. But unfortunately, many are not paying equal attention to the possibility that security designs may be compromised through IP theft or reverse engineering. Prudent suppliers will recognize and address this serious security gap with appropriate protection of their critical software. As the review of Irdeto illustrates, technology and support are readily available to help address this situation.
Cloakware is a registered trademark of Irdeto B.V. All other trademarks mentioned are the property of their respective owners.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Industrial IoT Cybersecurity, Software Hardening, Digital Transformation, ARC Advisory Group.

