

It’s reasonable for companies to be concerned about the security of IoT device deployments in industrial environments. Each device has an associated risk to data and operational integrity. A compromised inter-net-connected device could create a pathway for attacks on connected systems, including critical control systems.
While essential, secure-by-design IoT devices are not enough to manage all the risks. Threats to device security exist throughout the complex industrial IoT device supply chains. This includes compromised software from technology developers, poor security practices by OEMs, weaknesses in distributor security practices, poor security enablement by implementers, and insecure connections of devices to IoT platforms and cloud systems. Maintaining security throughout a device’s lifetime requires careful coordination with external suppliers and support groups. Companies need to understand these challenges and develop appropriate risk management strategies before widespread deployment of industrial IoT devices.
ARC Advisory Group held a workshop on this critical issue at the 2019 ARC Industry Forum in Orlando, Florida. Experts in various aspects of industrial IoT cybersecurity shared their insights and addressed attendee questions.
Demand for information about industrial operations has never been higher. Companies want data to understand and improve costs and productivity. Unlimited cloud storage, high-speed connectivity, and powerful analysis tools have created an explosion in improvement projects. Leaders of these initiatives want new sensors installed to monitor people, processes, and products and increased access to plant data stores.
Industrial product suppliers recognize the growing demand for information. Connectivity and ease of data sharing have become mandatory requirements for new applications and controllers. Networks are being upgraded with powerful new edge devices that support local data collection, analysis, and control. Smart assets, like robots and autonomous vehicles, are being designed for remote monitoring and support. All system elements are becoming industrial IoT devices that must be protected. While the benefits are clear, the explosion in connected devices under-mines the effectiveness of conventional industrial cybersecurity strategies. Perimeter defenses and isolation techniques are ineffective when every device can communicate with external services. Constraining open connectivity may be prudent, but it frustrates business leaders who need to reduce costs and address competitive challenges. Companies need strategies (other than avoidance) to deal with the cyber risks of industrial IoT devices.
IoT device technologies and capabilities vary widely. Some are simple sensors, while others are complex control systems. Security concerns differ, but users expect reliable and predictable performance from all IoT devices. This requires confidence in the initial and ongoing integrity of the device’s hardware, software, and critical information it may contain.
Ensuring that devices are secure-by-design is essential. Designers need to follow secure development lifecycle practices (SLDC) and devices need capabilities that protect against local tampering and compromising communications with external systems. Organizations like ISASecure and UL offer device certification services that help industrial IoT device suppliers demonstrate design security. Unfortunately, most devices still don’t have such certifications.
Industrial IoT cybersecurity strategy needs to cover more than secure-by-design devices. SDLC practices and designs alone can’t guarantee that a specific unit is free of malware, security features properly enabled during installation, certificates have been protected, connections with external systems are secure, and security is sustained during operation.
Industrial IoT supply chains are complex, with innumerable opportunities for security compromises. Enforcing security across every participant and handoff is often impractical, but managers can be made aware of the risks they are accepting before they deploy devices in an industrial environment. This can increase appreciation of security team concerns and garner support for basic cybersecurity controls like vendor qualification and pre-deployment testing of industrial IoT devices.
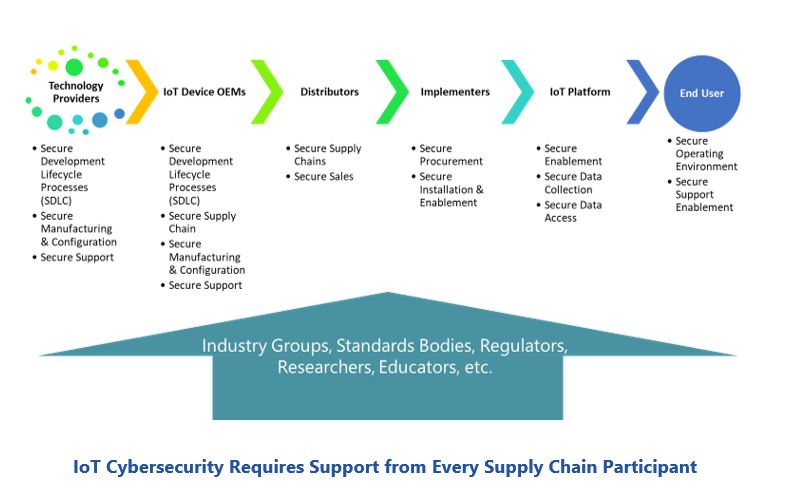
Supply chain participants are well aware of the importance of addressing end user security concerns. Without appropriate security, suppliers of industrial IoT devices and manufacturers of smart industrial equipment lose revenues and opportunities to sell new services, like remote support. Many are supporting industry efforts, like the Industrial Internet Consortium (IIC) and The Open Group, to develop common security frameworks. The US government shares this concern and supports resolution through NIST programs and funding of special projects, like FACT, to reduce the risks of compromised software throughout the supply chain.
A diverse group of five industrial IoT experts participated in the Industrial IoT Cybersecurity workshop at this year’s ARC Industry Forum in Orlando. They shared their observations on the state of industrial IoT cybersecurity and various efforts to address this challenging issue.
Marcellus Bucheit, President and CEO of Wibu-Systems is a member of the IIC trustworthiness task group. This group explores aspects of trustworthiness relevant to the IIoT and IIC's vision of an IIoT ecosystem.
Mr. Bucheit explained why trustworthiness should be the goal for users of industrial IoT devices. Trustworthiness is the degree of confidence one has that a device will perform as expected with respect to safety, security, privacy, reliability and resilience while facing environmental disruptions, human errors, system faults and attacks. In his experiences, IT and OT groups have restricted efforts to addressing only subsets of these requirements. Industrial IoT expands their perspectives and drives a shared understanding of the need for complete trustworthiness.
Camilo Gomez is Global Cybersecurity Strategist at Yokogawa and a member of the Open Process Automation Forum (a forum of The Open Group), which developed the standards-based, open, secure, interoperable process control architecture O-PAS[1]. This platform reflects the growing demand for control systems with openness, connectivity, and upgradability.
Mr. Gomez is co-chair of the security working group charged with developing requirements for security across the O-PAS Framework. Goals of openness, interoperability, and agnosticism mean that systems require security controls similar to industrial IoT devices.
Use of standards, a fundamental tenet of O-PAS, is reflected in how the security framework leverages various parts of the ISA/IEC 62443 standards set. This provides Design, Build, and Maintain security guidelines for technology providers and IoT device OEMs. The framework’s standards for secure connectivity have also been validated against the capabilities of OPC-UA and Redfish.
Eric Byres, CEO of aDolus, is well known in the ICS cybersecurity community for developing the Tofino firewall. He focused his comments on his current efforts to address the problems occurring in IoT software and firmware supply chains. Beyond malicious code and counterfeit software, companies don’t know what subcomponents are hidden in their products. Likewise, they have no easy way to determine if firmware upgrades are valid, free of vulnerabilities, and current.
Mr. Byres noted that information to solve this problem is available, but technicians need a quick way to access and use it to assess the trustworthiness of update files. Using a grant from the US Department of Homeland Security (DHS), aDolus created FACT, a community platform that aggregates information and provides a measure of trustworthiness similar to a FICO credit score. This platform supports the needs of vendors, asset owners, integrators, consultants, and security partners. He encouraged attendees to download complimentary versions of the solution to test its effectiveness and engage their organizations in the effort.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Digital Transformation, Industrial IoT, ARC Industry Forum, Cybersecurity, ARC Advisory Group.

