

For nearly two decades, we’ve seen considerable emphasis placed on the need to protect the integrity of the various elements of the critical infrastructure. In response to this imperative, industrial cybersecurity has become a well-defined discipline, complementing the more mature discipline of information security. While many of the practices employed in this newer discipline are like those used for information protection, others have evolved to address the specific characteristics and constraints of the industrial systems environment.
While many asset owners understand and have accepted the imperative to improve the security of their industrial systems, they still face significant challenges. Industrial cybersecurity is a complex and specialized subject that can be intimidating for those not deeply involved. The diversity of available sources of guidance further worsens the situation.
It is often difficult to select the specific guidelines and standards most appropriate for a particular situation and, once selected, it may be difficult to understand some of the complex associated concepts.
Just as with other technical disciplines, professionals working in industrial cybersecurity must do everything possible to clarify their message and explain their technology and practices to those requiring services in this area. It’s important to avoid unnecessary jargon and it helps to use a well-defined set of fundamental concepts.
The imperative to improve the security of automated systems employed in critical infrastructure has led to the emergence of industrial cybersecurity as a professional discipline. This complements the more established discipline of traditional information security. To secure complex industrial processes it is necessary to combine the skills and experience from traditional information security with those from instrumentation, automation, and process engineering to be able to identify the most effective response.
Although protecting critical infrastructure has been a primary driver, the practices associated with this developing discipline are also suitable to apply in less-critical sectors where ensuring the reliability and integrity of their processes is key to both safety and profitability. Sectors as diverse as petrochemicals, pharmaceuticals, and discrete manufacturing employ common automation systems and technology so it is reasonable to assume that security practices would also commonly apply.
While practices such as least privilege, defense-in-depth, and separation of duties have long been applied to secure business and enterprise systems, others have evolved or been adapted to address characteristics and constraints that are specific for industrial applications. To be most effective and appropriate in this context, these practices must be based on and supported by an appropriate set of policies, principles, models, and requirements. Collectively, these elements form a body of knowledge that provides the foundation for training and certifying experts in the discipline.
Although many available standards and guidelines provide much of this information, there are overlaps and possible inconsistencies. Several of the available resources remain industry- or sector-specific. Asset owners are unlikely to have the time or specialized resources required to become industrial cybersecurity experts. Those with operations that span multiple sectors may be confused as to what guidance is most effective for their situation.
Asset owners need simple and practical guidance to help take the necessary steps to improve the availability and resilience of their systems and associated processes. They must be free to spend less time trying to interpret and understand what is available to them, and more time to applying this information. While a considerable amount of information is available in the form of standards, practices and guidelines, there are often inconsistencies in some concepts and terminology. This leads to confusion and uncertainty when attempting to apply this information, which can then lead to an ineffective response.
In conversations with asset owners and end users, it is common to hear requests for checklists or similar documents that provide step-by-step direction as to the measures that are required to secure systems. Unfortunately, the complexity of the subject combined with the wide variety of possible configurations makes such an approach impractical for anything beyond the simplest of measures. Collectively, these simple measures are often characterized as “cybersecurity hygiene.”
Although these simple measures are important, they are not sufficient. Just as with other more traditional technical disciplines, assembling a comprehensive response must start with understanding and interpreting a set of basic concepts.
As the industrial cybersecurity discipline has matured, several fundamental concepts have emerged in widely accepted and adopted standards and practices. The terms used may be different, but the basics are essentially the same.
In all but the simplest of cases, industrial automation systems can be quite complex, consisting of a combination of hardware and software products and components, focused solutions (i.e., addressing a specific function), and smaller self-contained systems or subsystems. This can lead to confusion as terms like “system,” “solution,” and “product” are often used inconsistently or even interchangeably, resulting in confusion and lack of clarity.
Systems engineering provides methods to describe how such systems are constructed. It begins with defining the taxonomy that classifies the elements used to construct an industrial automation system and how they are related. In the case of industrial automation, the overall systems consist of one or more focused solutions (e.g., batch, optimization, etc.). Each of these solutions is constructed using one or more products that are in turn constructed using components.
Just as a taxonomy helps characterize the technology used to create automation systems, principal role descriptions can help describe the people dimension. Although people may serve in many roles in the operation of cybersecurity management systems, a small number of principal roles must be clearly defined. Each may be described in terms of the activities it performs and its duties (responsibilities or accountabilities).
The cybersecurity response must address all phases of the product, system, and solution lifecycles, from conception, development and delivery of products and systems through their implementation, operation, and support.
Product and technology suppliers use a product lifecycle that requires them to take the necessary steps to ensure that, to the extent possible, their products are “secure by design.” Although such products can operate securely in an integrated system, it is still possible to deploy and operate them in a less-than-secure manner. The asset owners and service providers must address security during specification, integration, operation, and support.
Understanding lifecycles and how they are connected is essential to secure automation systems. Suppliers must share the capabilities and limitations found during development with customers, and asset owners and service providers must share their experiences with suppliers to allow them to improve the security of their products.
Most industrial cybersecurity standards and guidelines identify the need to segment complex systems based on assessed risk. This is essential as all but the simplest of industrial automation systems include many subsystems and components employed to control various parts of the underlying process. Just as with safety protection, the risks associated with some segments are higher than with others. Although the threat and vulnerability components of risks may be common, the consequences are not.
Methods and tools such as process hazard analysis (PHA) used in safety systems design are often adapted to assess security risk. With the results of these analyses it is possible to segment a complex system and apply compensating countermeasures that complement the intrinsic security of individual elements. The use of powerful firewalls or unidirectional gateways in high-risk portions of the network is a common example.
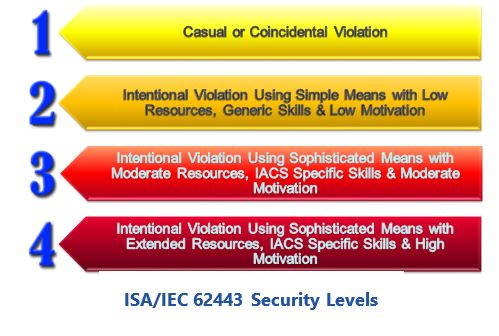
The ISA/IEC 62443-3-2 standard describes a detailed approach to risk assessment and system segmentation. Approved by both IEC and ISA, this standard is expected to be available later this year.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Concepts, Principles, Requirements, Industrial Cybersecurity, ARC Advisory Group.

