

Cybersecurity concerns are impeding digital transformation and Industry 4.0 initiatives in industrial and critical infrastructure organizations. Managers recognize that even well-designed IoT devices can be compromised. They also understand that increased connectivity of IT, OT, cloud and third-party systems give attackers more access to critical systems, increasing the risks to safety, operational performance, and intellectual property.

While technology isn’t a panacea, continuous OT network security monitoring can help companies deal with many of these security management challenges. Developed for complex industrial control systems, this technology supports a wide range of IT, OT, and IoT devices with various operating systems, security capabilities, and communication protocols. It can help security teams detect and identify unknown devices; maintain accurate asset inventories; identify vulnerabilities and assess risks; and, provide time for defenders to sustain defenses with patches and compensating controls. Continuous monitoring features also give defenders advanced notice of suspicious or unauthorized network traffic and unexpected device changes, providing time to respond to attacks before critical operations are impacted.
ARC Advisory Group recently discussed the security challenges of digital transformation and Industry 4.0 with CyberX executives. As we learned, recent updates to the CyberX industrial cybersecurity platform are designed to address many of these issues.
ARC’s industrial/OT cybersecurity maturity model demonstrates the many ways that continuous OT network monitoring can help companies manage security challenges. While developed for OT cybersecurity programs, this model is equally applicable to digital transformation and IoT security.
ARC’s model breaks cybersecurity into a sequence of steps that an organization needs to pass through to establish a program that achieves its risk management goals. Each step has an associated set of people, 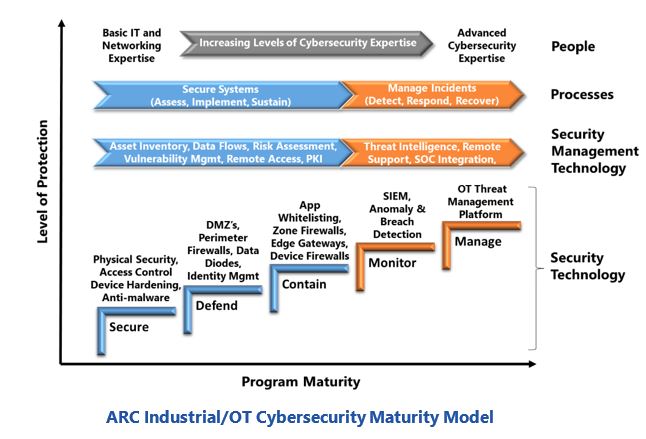
Continuous OT network security monitoring is an enabler for every cybersecurity maturity step. It’s asset discovery and inventory capabilities provide the starting point for actions taken at the Secure level. Advancements to Defend and Contain require its deep understanding of data flows within the system and across system perimeters. Its ability to compare messages with established baselines is the essence of anomaly detection, the additional protection provided by the Monitor maturity level. Continuous message information is also a foundational requirement for the forensic investigation and remediation activities performed in the Manage maturity level.
Small operating margins and stiff competition require industrial companies to continuously improve performance and reduce costs. Seaports, airports, and other transportation organizations are also under constant pressure to increase safety while improving the delivery of vital services. Smart buildings and data centers require access to real-time sensors and controllers to reduce costs and environmental impact.
Today’s explosion in unmanaged IoT devices, connectivity, cloud services, and analytics provides an opportunity to lower costs and enhance performance. Digital transformation, the umbrella term for these opportunities, is fueling broad deployment of new, potentially insecure IoT devices and broader connectivity among OT, IT, and Cloud systems.
Digital transformation initiatives for industrial and critical infrastructure organizations involve a wide range of network connectivity changes (such as wireless and cloud) and specialized cyber assets. Security teams need to anticipate new connections between IT and OT systems in plants, buildings, transportation systems, etc. In many cases, new IoT devices incorporate industrial technology, like PLCs, that collect data from simple sensors and manage local equipment like pumps, robots, and conveyance systems.
Industrial equipment has limited capabilities to support conventional cybersecurity technology, so security requires constant vigilance. Changes in devices and connections need to be detected rapidly, assessed for vulnerabilities, and addressed before the organization’s security erodes. Network connections need to be monitored continuously to detect unauthorized or suspicious traffic, scanning activities indicating potential cyber espionage, unusual remote access, and lateral movement efforts between systems. Automation is essential to deal with the explosion in assets and network connections, as is selecting a solution that addresses these challenges.
Conventional IT network monitoring methods are not adequate for mixed IT, OT and IoT environments. Users require technology that supports diverse assets with limited security capabilities; conventional and unconventional operating systems; and a collection of conventional and proprietary IT, ICS, and IoT protocols. Continuous OT network security monitoring was developed specifically to address these kinds of environments.
Passive, agentless network security monitoring and Layer 7 deep packet inspection (DPI) capabilities of continuous OT network monitoring solutions allow safe, in-depth monitoring of OT assets, systems, and networks. Anomaly detection capabilities also alert defenders of policy violations such as the connection of unauthorized laptops to the control network and unexpected communications such as “PLC STOP” commands and PLC logic updates. While extensions may be needed to support new IoT devices and protocols, this is a common challenge for continuous OT network monitoring solution providers. The same is true for integration with different IT security tools, like SIEMs.
In addition to reducing security risk, continuous network monitoring provides OT teams with additional benefits. First, it provides deep visibility into network and device behavior enabling OT teams to perform root cause analysis for misconfigured or malfunctioning equipment, such as devices unnecessarily consuming large amounts of network bandwidth. Second, it provides an up-to-date inventory of assets, enabling organizations to save money by minimizing spare parts for devices that are no longer being used. Third, it supports the core OT values of ensuring safety and minimizing downtime by immediately alerting teams to any unusual or unauthorized behavior that can impact OT environments.
Founded in 2013, CyberX has a long history in continuous OT network security monitoring. The company has a team with deep expertise in IoT/ICS cybersecurity and specialized threat intelligence. Its CyberX platform is used to protect industrial and critical infrastructure facilities across the globe, across a wide range of industries (manufacturing, pharmaceutical, chemical, energy & water utilities, oil & gas, transportation, building management, etc.) and supporting a wide range of automation products from leading automation suppliers.
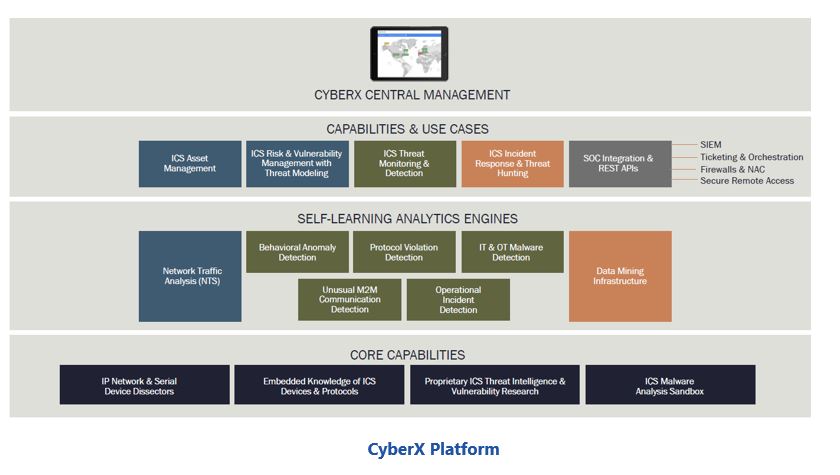
The CyberX platform provides the capabilities needed to monitor, assess, and manage security in mixed IT, OT, and IoT environments. The platform is agentless and doesn’t require configuration of rules or signatures or previous knowledge about the environment. The platform can auto-discover assets with passive monitoring to create an up-to-date asset inventory with key information like device type, manufacturer, protocols used, open ports, serial number, and firmware revisions. An optional Active component uses safe, vendor-approved commands to query both Windows and controller devices for additional asset details. The CyberX platform also has capabilities to assess overall cyber risk and produce a vulnerability assessment report that includes an objective risk score along with prioritized, detailed, and actionable mitigation recommendations. This provides a basis for security management and a means to assess continuous improvement in reducing IoT/ICS risk.
In addition, by leveraging a unique CyberX capability called automated threat modeling (attack vector simulation), security teams can visualize the most likely paths attackers would take to compromise the organization’s “crown jewel” assets — ranked by risk — and then use this information to prioritize their mitigation activities, such as patching and network segmentation. This enables more effective use of limited human resources and the availability of maintenance windows by focusing mitigation activities on protecting an organization’s most critical assets whose compromise would have a major financial, safety, or environmental impact.
Continuous monitoring in the CyberX platform leverages five separate but integrated analytics engines. This provides owners with:
Integration of IT and OT security workflows is essential for effective security management in the mixed environments created by digital transformation. The CyberX platform supports this with out-of-the-box integrations with a variety of widely-used security technologies and management tools in which enterprises have already invested to run their Security Operations Centers (SOCs). These include:
CyberX’s Central Manager provides users with a consolidated view of all assets, alerts, and security risks. The product supports multiple geographically-distributed sites, different asset groupings based on location, business unit or custom groupings, customizable filters, data mining, and a timeline view of alerts and events that allows defenders to correlate and identify root causes across assets, systems, and global facilities. This product also provides centralized management of CyberX sensor appliance settings, threat intelligence, and software updates.
CyberX customers include large and complex organizations worldwide. Named references include Teva Pharmaceuticals, SGN (formerly Scotia Gas Networks), Adani Power, Deutsche Telekom, Toshiba, and First Quality Enterprises (a CPG manufacturer with 5,000 employees). Other notable references include two of the top five US energy utilities; a top-five pharmaceutical company, and a Fortune 500 chemical company with plants worldwide; leading transportation organizations and oil & gas firms; and multiple US government agencies and national labs.
To help customers with limited internal resources manage IoT/ICS security on their own, CyberX has also partnered with leading service providers and MSSPs worldwide including IBM Security, Optiv Security, DXC Technology, GrayMatter, Singtel/Trustwave, T-Systems, Toshiba, and Wipro.
While digital transformation projects offer significant benefits, they also increase the risks of a costly and/or dangerous cyber incident. Deploying unmanaged IoT devices will expand the attack surface and increased connectivity will facilitate attackers’ efforts to access critical systems. As defensive options are limited, security teams need to continuously monitor all devices and network traffic flowing within critical systems. Continuous IoT/ICS network security monitoring was designed for systems with mixed IT, OT, and unmanaged IoT devices. The technology’s value has been proven in a variety of complex environments. Security teams should consider how they can leverage this technology to address reducing the cyber risks associated with digital transformation.
These new developments will impact every industrial company in some way. It’s naïve to assume that digital transformation leaders will continue to delay rollouts over cybersecurity concerns. Security teams need to act now to ensure that they don’t lose control of the organization’s security. Our brief review of CyberX shows that practical, effective and comprehensive solutions are available to address these needs.
.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Continuous OT Network Monitoring, Digital Transformation, Industrial/OT Cybersecurity, IoT, CyberX, ARC Advisory Group.

