

DHS recently held several webinars in the wake of its March announcement regarding Russian state-sponsored hacking group Energetic Bear/Dragonfly on utilities and critical infrastructure installations in the US. Recent comments from DHS officials indicate that these attacks had hundreds of victims and demonstrated the ability of these groups to gain operational control of critical infrastructure industrial control systems (ICS). The National Cybersecurity and Communications Integration Center (NCCIC) recently held a series of webinars that addressed Russian activity against critical infrastructure, with the last webinar held on August 1. You can download the slides from the webinar here.
The webinar focused on some of the more interesting and unique aspects of these recent attacks plus some countermeasures that end users can implement right now that can greatly reduce the likelihood of future attacks. A detailed explanation of the attack methodology can be found in this DHS publication NCCIC Alert TA18-074A. According to NCCIC, reconnaissance, SMB-based spear phishing and waterhole attacks, and exploitation of single-factor authentication were key elements used in these attacks that claimed over 100 victims. Exploitation of trusted vendors to get specific information about the types of control systems used at these installations is another unique feature of these attacks. The attackers were then able to gain access to industrial control systems by retrieving credentials for those systems through access to corporate networks.
This access, however, is typically preceded by intelligence gathering and reconnaissance activities, including secondary research on the Internet to identify specific control systems that may, for example, be posted in photographs on corporate websites or any other information that can be gathered through open, public domain sources. Spear phishing, as we have seen so many times before, is the preferred method of these attackers to steal credentials and gain access to corporate networks. Armed with the knowledge of the specific control systems operating at these facilities, the attackers could then browse the corporate networks to find information related to the control systems, such as user credentials, configuration files, and other types of documentation.
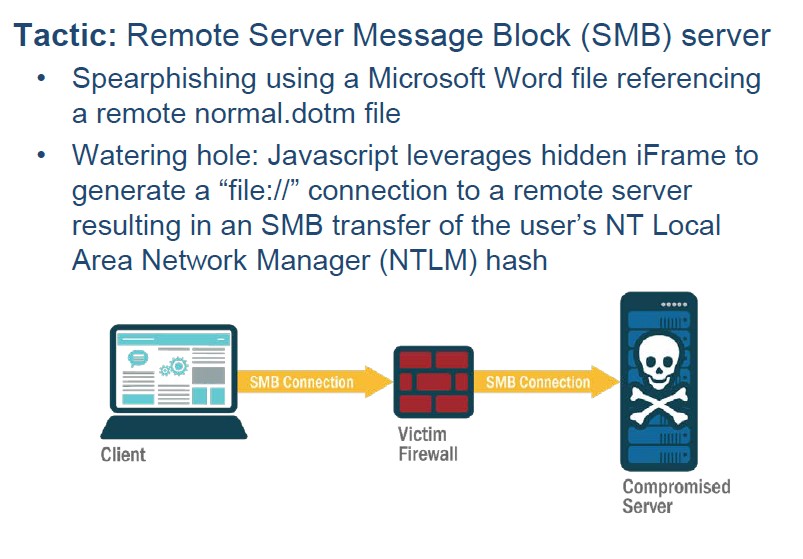
Spear phishing, in other words, a phishing campaign launched against a specific chosen target, was the primary method for credential harvesting. This spear phishing technique involves a Microsoft Remote Server Message Block vulnerability where the attacker sends a legitimate Microsoft Word doc that references a remote normal.dotm file. Essentially, when the user accesses the Word document their credentials are automatically sent to the compromised server. The watering hole also used the SMB vulnerability through a hidden iFrame in JavaScript to generate a connection to the remote server. Once credentials were harvested, there were three known intrusion vectors, including Outlook Web Access (OWA), corporate virtual private networks (VPNs), and remote desktops.
As NCCIC points out, all victims had externally-facing, single-factor authenticated systems. Use of multi-factor authentication would have gone a long way toward stopping these attacks. However, as we saw with the recent hack on Reddit, even multi-factor authentication alone is not enough. The Reddit hack exploited a vulnerability in its two-factor authentication system where SMS messages containing verification codes were texted to employee cell phones whose SIM cards were compromised using a “SIM-swapping” attack, allowing the attackers to take control of employee SIM cards and gain access to all data being sent to the phone. This type of authentication might be fine for some applications, but for high-level users with access to critical aspects of an enterprise, the use of key-based two-factor apps or keys. Google made headlines recently with the implementation of the Titan Security Key that has essentially neutralized phishing at Google.
NCCIC had many other recommendations, from implementing more active monitoring of threats to blocking all external SMB network traffic. End users should search for known indicators in historical logs and remain focused on behaviors. NCCIC also recommended that end user stop whitelisting network traffic with trusted partners.

