

It is often forgotten that North American rural communities have the same cybersecurity challenges as large cities. Cyber-attacks, most frequently in the form of ransomware, made big headlines when they affected cities like Atlanta and Baltimore. The Atlanta attack, for example, disrupted many key city services. Various sources report the total cost of that attack at between $12 million and $17 million.
While attacks on large US cities have had significant financial and operational impact, these same kinds of attacks, on a much smaller scale, can have a much more significant impact on smaller, more rural communities. The recent malware attack on 22 Texas communities is a recent example of this. Back in August of 2019, this attack was the first coordinated ransomware attack on multiple communities simultaneously that appears to be the work of “one single threat actor,” according to the Texas Department of Information Resources (DIR).
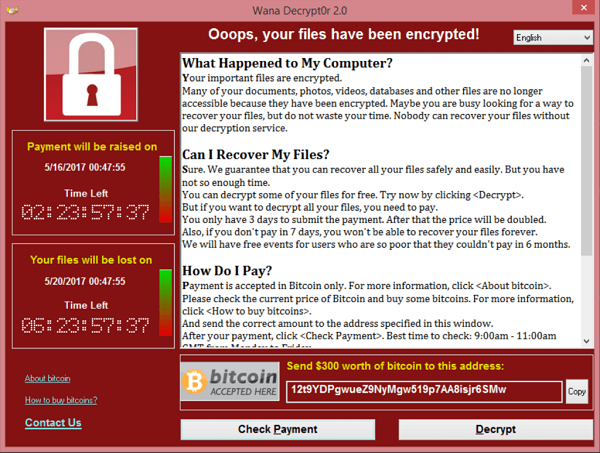
Attackers seemed to target specific departments within the towns. Many key business and financial functions of these communities were paralyzed, including access to birth and death certificates, while some towns were unable to process utility payments. Let us look at how these communities responded and what must be done in the future to prevent these attacks.
The Texas communities did have one thing on their side – the assistance of the Texas Department of Information Resources (DIR). The status at the Texas DIR State Operations Center (SOC) was activated to Level II Escalated on the morning of the attack. According to the DIR statement, the “coordinated state and federal response to a statewide, multi-jurisdictional cybersecurity event was the first of its kind and was a tremendous success.”
In addition to coordination with DIR, the state also had the assistance of two cybersecurity teams from the Texas A&M University System. The Texas A&M system includes 11 universities, and the system is constantly under attack, blocking ransomware attacks daily. Cybersecurity experts from the FBI, FEMA and the Texas Military Department were also involved.
One reason for this success was a good response plan. DIR already had a response plan in place and that was immediately put into action. Within hours of receiving notice of the event, state and federal teams were executing the plan and in the field at the most critically impacted sites to begin eradicating the malware and assessing impact to systems. By day four, response teams had visited all impacted sites and state response work had been completed at more than 25% of those sites. One week after the attack began, all sites were cleared for remediation and recovery.
Reports indicate that the attackers got in through outsourced IT software providers, which are used by many of these small communities since they do not have the budget to fund their own IT departments. It does not matter if you are large city or small community, you must take the time to evaluate the security of your partners, both at the IT and OT level. The partner selection process should be driven by relevant criteria and should be approached as a lifecycle process. Evaluation of a partner’s competence in cybersecurity is not a one-time exercise at selection. It must be periodically reverified.
Ransomware attacks have accelerated this year, as more criminal organizations are realizing that cities, towns, hospitals, and small businesses, are easy prey. Being easy prey, however, doesn’t mean that attackers are indiscriminate. More coordinated attacks against preselected targets are becoming more common. A successful ransomware attack is also an indicator that there are many other underlying security issues within the organization that must be addressed. Ransomware attacks are almost always spawned by successful phishing attacks that deploy other forms of malware that allow the ransomware to be deployed. Surviving a ransomware attack should be viewed as a wake-up call to reevaluate cybersecurity practices and strategy throughout your organization.

