

Several ARC analysts attended ABB Customer World earlier this month in Houston at the George R Brown Convention Center. ABB Customer World is by far the largest user group meeting for any single process automation supplier. With over 10,000 people in attendance, ACW featured a huge exhibition space with the common theme of ABB Ability Internet of Things technology, as well as the capabilities of the recently acquired B&R Industrial Automation. Other alliance partners like Hewlett Packard Enterprise and their edge computing products were also very evident, as well as a mind-boggling array of products and solutions from the power transmission and distribution business to power generation systems, electrification, drives, process automation, and industry-specific solutions. This year’s event featured a much stronger cybersecurity message, with products and solutions on display as well as a solid track of presentations and panel discussions on cybersecurity that lasted throughout the week.
ABB’s has an alliance with ICS cybersecurity supplier SecurityMatters and its SilentDefense offering, which was recently acquired by Forescout. ABB’s Cyber Security Asset Inventory solution was on display in multiple areas of the exhibition space, to showcase added benefits as a result of leveraging the SilentDefense technology with ABB’s ICS expertise in one solution. SilentDefense is a hybrid solution that blends behavior-based and policy-based anomaly detection approaches.
ABB Cyber Security Asset Inventory uses technology that automatically and inherently identifies the cyber asset, and captures inventory information such as ports, services, and software. Cyber Asset Inventory provides up-to-date information on control networks and can help in decision-making for incident response, asset lifecycle and management concerns. One of the primary goals of Cyber Security Asset Inventory is to automate not just scanning tasks but also data collection and reporting tasks, which greatly reduces the number of labor hours dedicated to cybersecurity and allows personnel to focus on higher value tasks.
Mandiant/FireEye was one of the first cybersecurity suppliers to report on the TRITON/TRISIS process safety system malware attack back in 2017. Rob Caldwell leads Mandiant’s industrial control systems consulting practice and gave an in-depth presentation on the timeline leading up to the event as well as the response and best practices to avoid such attacks in the future. Robert talked about the TRITON malware incident and it unfolded, as well as how hacker techniques have evolved since Stuxnet. Robert pointed out, as ARC has also pointed out in the past, that there were many things that the asset owner might have noticed that would have tipped them off to the attack early, and there were many best practices and procedures that were not followed at this facility that would have prevented the attack.

Randy Howard of Microsoft’s cybersecurity practice gave an in-depth presentation that covered both Microsoft’s overall cybersecurity capabilities and spoke about how the cloud can actually be leveraged to provide better cybersecurity with remotely managed applications. Many people don’t realize that Microsoft has significant cybersecurity capabilities. Mr. Howard also provided a good overview of the overall cybersecurity landscape as we head into 2019. Mr. Howard pointed out that ransomware attacks actually decreased between 2017 and 2018.
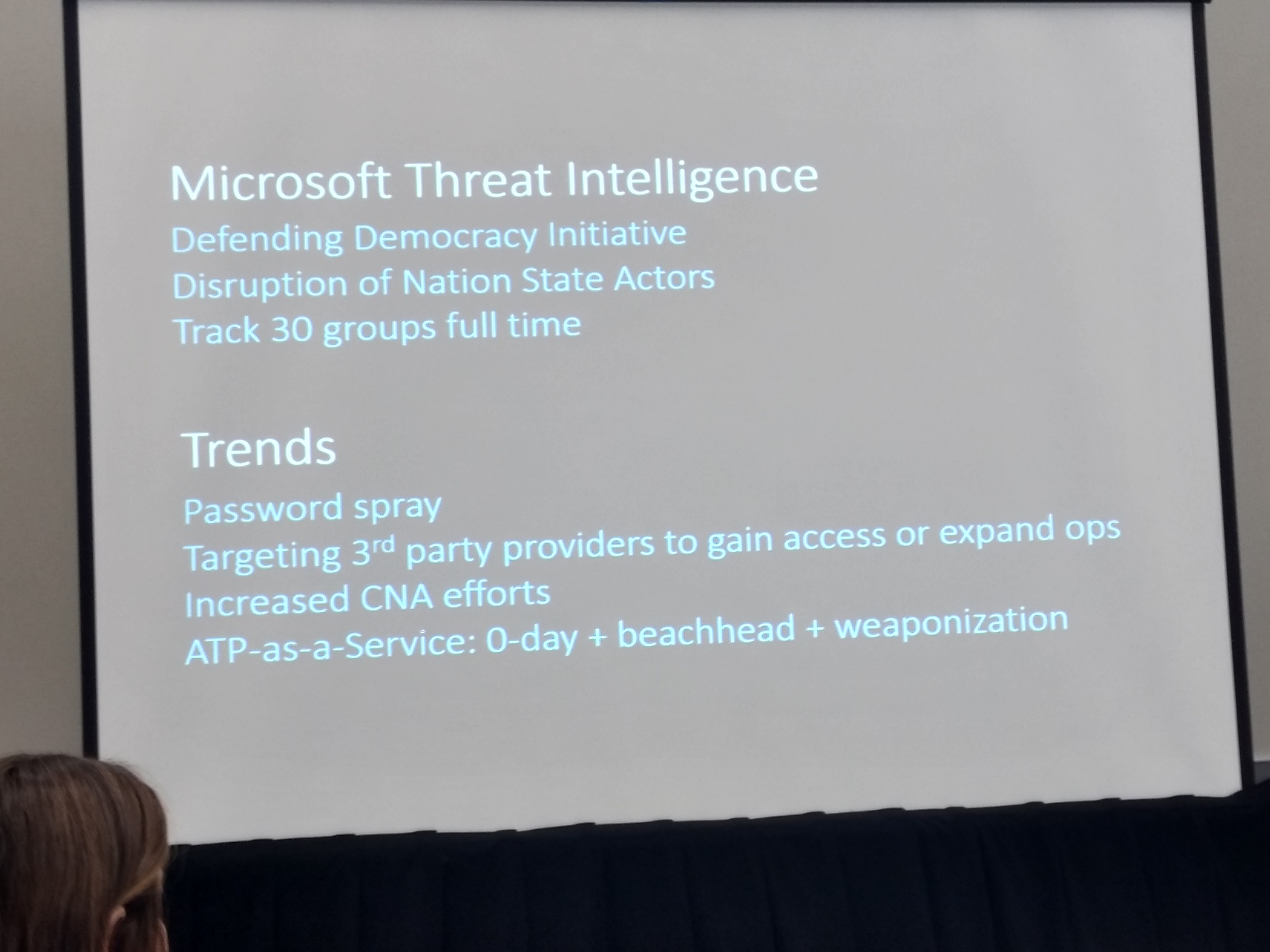
ARC also participated in a Panel discussion with Ragnar Schierholz, head of cybersecurity for the Industrial Automation division of ABB, Torey Smith of Hemlock Semiconductor, and Randy Howard of Microsoft. The discussion was all-encompassing and ranged from simple first steps toward implementation of a good cybersecurity program, the impact of IT/OT convergence on cybersecurity, and sharing opinions on today’s largest looming cybersecurity threats. Hemlock Semiconductor gave a very good end-user perspective on what it takes to implement an effective cybersecurity program and how to facilitate communication between the IT and OT domains.

